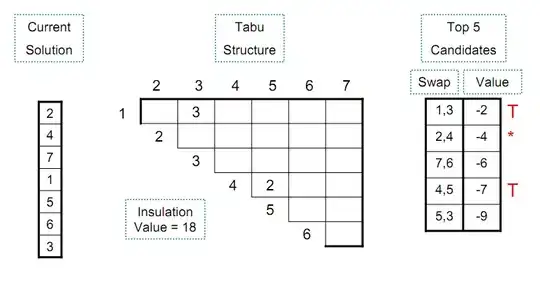
We have a working MDM solution, where enrolling devices and installing profiles works. However since iOS 5 customers have reported that the selfsigned certificate we use is reported as Not Trusted on the devices. Users that had the certificate and profiles installed on iOS 4 reports that is looking correct when they upgrade to iOS 5, as long as they don't re-enroll.
I have been able to reproduce this and taken the following screen dumps.
First I install the needed MDM root certificate. After installing it the root certificate appears to be trusted and looking at the details everything looks correct.



The next I do is to install a profile. At first the profile appears verified and I continue to installing it. When the install finishes the profile is no longer verifed and instead it is reported to be unsigned.

Then I go back to the root certificate and now the certificate is no longer trusted. If I click to see the details all information about the certificate is gone.
When the enrollment has finished we are able to install and delete profiles on the device, however we see these warnings about the certificate not being trusted and the profile being unsigned
If I choose to reinstall the root certificate I can do that and I get the details back, a certificate that is reported trusted and a profile that is verified.
I have looked into our SCEP implementation trying to find the problem, but with no luck. Whenever I make changes to what is returned to the device, the device reports to me that what it receives is not valid. This makes me think that what we are sending is actually correct, since the device reports when there is a problem.
Has anyone seen problems like this, or do you have a possible explanation?
Edit
Maybe somebody has an idea about what type the self signed certificate should be? The one used in the screen schots below is x500 v1. If I create a X509 v3 (with extensions or not) the iOS device does not trust it no matter what.