I need an authentication/authorisation module for my SaaS web app and am liking the look of WIF. The problem is that apart from Active Directory there doesn't seem to be a plug and play way to serve claims. My idea is to use IdentityServer and replace the ASP.NET Membership Provider repository with my own one.
The trick is
- The app Internet facing with many different customers. (So ADFS2 is not applicable).
- I want granualar operation level permissions, not roles. (So ASP.NET Membership is not suitable)
- I want the users within my app to manage their own subset of users.
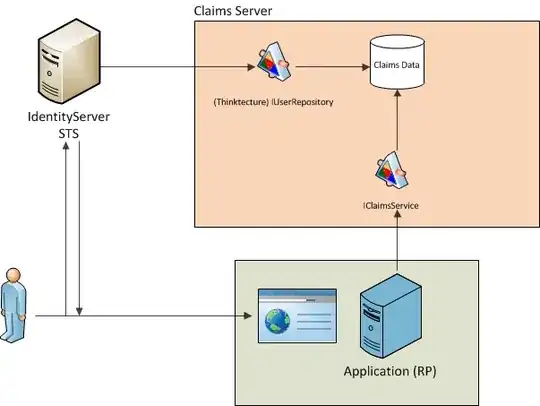
The bit I intend to build is the pinky coloured box below called the 'Claims Server'.
IClaimsService would allow things like creation of new users, creating roles, assigning permissions to roles and assigning users to those roles. My own application would auth the admin screen that plugs into the IClaimsService and auth a users permission to create a sub user etc.
My question is - is this a valid architecture or am I completely missing the point of WIF?
or is there an alternative plug and play option that I haven't found? I'm happy to not reinvent the wheel!
Additional Info
My web app is a SaaS which needs to allow my customers to create their own users within their own walled garden of data.
Think for example of a recruitment software platform where you have competeting teams of recruiters who have their own clients in the system. One team is not allowed to peak at another teams data but each team can manage and administer their own subset of users. There could be many different companies using the platform so there is not a central IT dept / Domain that would administer this. It's all self service.
I've had a look at netsqlazman which is close to what I want but Windows Identity Foundation looks like it will have more long term benefit as I wire in new customers and could connect their own STS to mine for authentication.