I recently read the the following SO question.
What's the best way to store a password or private key on a web host?
It mentions encrypted connection strings (for use in an ASP.NET app) or using the Data Protection API (DPAPI) at the time of this writing. Both seem like good solutions for this user's particular use case.
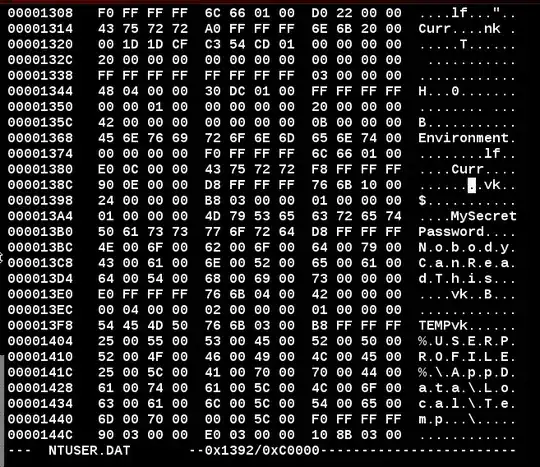
However, traditionally I've always stored sensitive configuration values like passwords and connection strings in User Environment Variables on the server(s) they are being used on. These are easy to define, change, and read (from an IT perspective). They're also easy to access regardless of the framework or language used.
The question is: Is it good practice to store sensitive data in windows user environment variables and if not, why?
EDIT:
Based on Ken's comments a pre-requisite question should be: Is the windows registry contents encrypted?