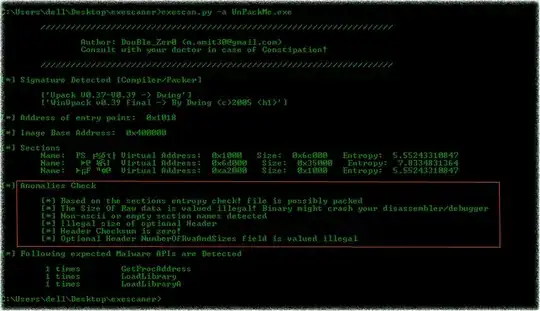
I've found an application which seems to be packed. I opened it with some hex editor and it contains "UPX1" section and "3.00 UPX!" string. Unfortunately I'm not able to decompress it with upx latest, it says "not packed by UPX". Is there a way to find out what other PE compressors/crypters were used?
Asked
Active
Viewed 3.0k times
3 Answers
13
PEiD is the tool you want. It can detect a variety of unpackers, attempt to unpack any packed exe (regardless of packing scheme), do simple disassembly, detect encryption algorithms present in the source code (not the encryption scheme of the exe, to be clear), and more. But primarily, it is an identifier of packers, cryptors, and compilers of an exe.
Universitas
- 493
- 2
- 5
- 21
erjiang
- 44,417
- 10
- 64
- 100
-
PEiD has been discontinued according to the wiki. An older version is still available for download according to http://www.aldeid.com/wiki/PEiD – Universitas Jul 08 '13 at 18:20
1
In many cases, a packaged executable starts with the launch program, followed by a standard zip file. This is possible because the ZIP header is at the end of the file, so you can prepend arbitrary data to a zip file, and it remains to be a zipfile. So try unzipping it, and see whether that works.
Martin v. Löwis
- 124,830
- 17
- 198
- 235
-
Unfortunately that is not my case. It's not a zip file, the program isn't a standard "self-extracting" archive, it's rather packed with some other PE packer, and ALSO an UPX (as I mentioned above, the UPX header is also present). – migajek Aug 13 '09 at 12:44