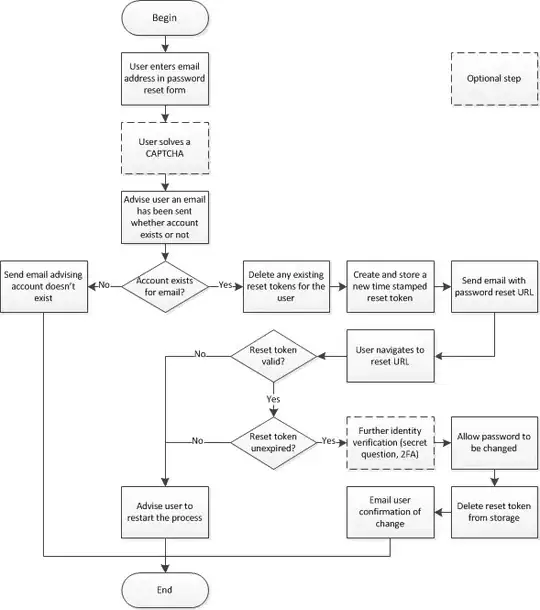
I am working on a C# ASP.MVC 4 project making use of the DefaultMembershipProvider and I am trying to come up with a user friendly way to recover / reset a lost password.
My first attempt was to have the user provide their username (which is a valid email address) the application would then generate a random password (meeting our requirements), that password is then emailed to the user.
My ideal solution would be that when a user clicks the forgot password button. They are asked for their username which when provided would cause an email to be sent with a URL (this URL will also have an expiration date attached to it). This solution also resets the users password inside then application (before sending the email). When the user clicks on the URL, they are automatically logged in and sent to the change password form. Are there problems with this solution?
For configuration I have the following values set:
<membership defaultProvider="DefaultMembershipProvider">
<providers>
<clear />
<add name="DefaultMembershipProvider" type="System.Web.Providers.DefaultMembershipProvider, System.Web.Providers, Version=1.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" connectionStringName="DefaultConnection"
enablePasswordRetrieval="false"
enablePasswordReset="true"
requiresQuestionAndAnswer="false"
requiresUniqueEmail="false"
maxInvalidPasswordAttempts="5"
minRequiredPasswordLength="6"
minRequiredNonalphanumericCharacters="0"
passwordAttemptWindow="10"
applicationName="/" />
</providers>
</membership>