I'm having some trouble calling a web service from within a web application and I was hoping someone here might be able to help. From what I can tell, this seems to have something to do with the Kerberos double-hop issue. However, if it is, I'm not sure what to do to actually fix the problem. To make things harder, I don't have the proper permissions to make changes to Active Directory accounts, so I need to know what to ask for when requesting changes. In my situation, I need to pass the credentials (Integrated Windows Authentication) from a web application onto a backend web service so that the web service runs under the proper user context.
Here's my exact issue:
This works

This doesn't work
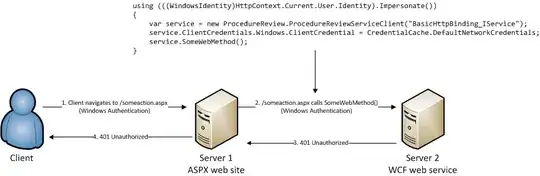
The only difference between the working scenario and the non-working scenario is that the working scenario is running the application on localhost (whether a developer's PC or on the server in question) and the non-working example is running on another machine. The code between both scenarios is exactly the same.
What I've tried
- Adding an SPN to the domain account that runs the app pool for each server
setspn -a http/server1 DOMAIN\account - Different methods of impersonation
- Removing the impersonation code
using(...)and executing the web service call as the app pool account. This works as expected.
Does anyone have any idea on what I might be able to do in order to fix this problem?