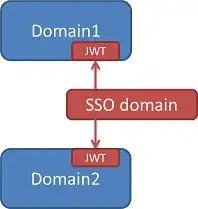
How can I implement a cookie based single sign on without a sso server? I would to share the user logged in across multiple applications using only a cookie on the browser.
In my mind it's working like this:
- user logs in an application
- the application verifies the credentials and then it setting up a cookie on the browser storing the username (that could be coded with a private key)
- if the user opens another application, it searches the cookie and reads the username on the value (using the key for decode the string)
In this solution a user may see the browser cookie (of a another user) and take the string codified of the username. Then he could adding it on an own cookie (no good!).
There's some secure way to do this? With a timestamp based control or something like this?
Thanks in advance.
Bye
P.S. I know that my english isn't very well.. sorry for this!