I was wondering how I can generate a strong and secure password in C#.
I googled a little bit and saw this formula in Wikipedia, where L is the length of the password and N is the number of possible symbols:
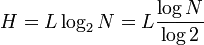
Also, I've found this question, but for some reason the method Membership.GeneratePassword just returns a random number with 1 digit, which absolutely no password. All the rest solutions, were very slow (>= 0.5 secs).
I need help implementing this formula (I don't know where to start). You may also suggest another solution or explain why the GeneratePassword isn't working.