... but when I make a request to https://example.com, it only responds in some browsers/devices...
OK, the certificate chain looks OK. I grabbed your server's name out of the cert you posted for the tests below. You can run your certificate through openssl x509 and see the CN and SAN:
$ openssl x509 -in server-cert.pem -inform PEM -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
79:e7:b4:bb:04:b2:49:e3:57:3a:42:3e:05:4a:0c:33
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=US, O=GeoTrust Inc., CN=GeoTrust SSL CA - G2
Validity
Not Before: Jun 11 00:00:00 2014 GMT
Not After : Jun 11 23:59:59 2015 GMT
Subject: C=ES, ST=Malaga, L=Malaga, O=Example, CN=www.example.com, OU=Example, LLC
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:a2:f6:fd:b0:30:10:91:55:3f:ec:ce:fa:d8:9e:
84:cd:60:c4:dd:a8:f0:42:37:66:a9:98:80:35:d8:
...
13:db:e9:98:c5:1a:ac:31:50:70:e1:6e:8d:1f:2a:
7d:b5
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Alternative Name:
DNS:www.example.com, DNS:example.com
X509v3 Basic Constraints:
CA:FALSE
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 CRL Distribution Points:
Full Name:
URI:http://gb.symcb.com/gb.crl
X509v3 Certificate Policies:
Policy: 2.16.840.1.113733.1.7.54
CPS: https://d.symcb.com/cps
User Notice:
Explicit Text: https://d.symcb.com/rpa
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Authority Key Identifier:
keyid:11:4A:D0:73:39:D5:5B:69:08:5C:BA:3D:BF:64:9A:A8:8B:1C:55:BC
Authority Information Access:
OCSP - URI:http://gb.symcd.com
CA Issuers - URI:http://gb.symcb.com/gb.crt
Signature Algorithm: sha1WithRSAEncryption
52:60:0e:f3:c7:fb:16:49:cf:4f:7c:91:d9:c9:b9:d5:92:62:
75:c9:05:f1:b7:cf:ea:30:53:44:5d:a7:1e:c7:eb:fd:a9:ab:
...
e4:4e:6b:b9:41:8f:c5:07:d0:8c:98:8c:b9:81:ad:b7:b5:c8:
ca:ff:0a:68
You have both example.com and www.example.com. That is OK.
One small nitpick. Placing a DNS name in the Common Name (CN) is deprecated by both the IETF and CA/Browser forums. DNS names should be placed in the Subject Alternate Name (SAN). Put a friendly name in the CN because its usually displayed to the user.
The issue should not produce the problem you are experiencing. In fact, I use Startcom certificates for my web and mail server and have never had an issue.
Next, OpenSSL's "Verify return code: 20 (unable to get local issuer certificate)" complaint is because you are not using CAfile option with <Equifax Secure Certificate Authority>.pem. If interested, you can download it from GeoTrust Root Certificates. I'll use it below to ensure a "Verify return code: 0 (ok)".
Now, check this out (SSLv3):
$ echo -e "GET / HTTP/1.1\n" | openssl s_client -connect example.com:443 \
-ssl3 -ign_eof -CAfile Equifax_Secure_Certificate_Authority.pem
CONNECTED(00000003)
depth=3 C = US, O = Equifax, OU = Equifax Secure Certificate Authority
verify return:1
depth=2 C = US, O = GeoTrust Inc., CN = GeoTrust Global CA
verify return:1
depth=1 C = US, O = GeoTrust Inc., CN = GeoTrust SSL CA - G2
verify return:1
depth=0 C = ES, ST = Malaga, L = Malaga, O = Example, LLC, CN = www.example.com, OU = Example, LLC
verify return:1
---
Certificate chain
0 s:/C=ES/ST=Malaga/L=Malaga/O=Example, LLC/CN=www.example.com/OU=Example, LLC
i:/C=US/O=GeoTrust Inc./CN=GeoTrust SSL CA - G2
1 s:/C=US/O=GeoTrust Inc./CN=GeoTrust SSL CA - G2
i:/C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
2 s:/C=US/O=GeoTrust Inc./CN=GeoTrust Global CA
i:/C=US/O=Equifax/OU=Equifax Secure Certificate Authority
---
...
Start Time: 1407401571
Timeout : 7200 (sec)
Verify return code: 0 (ok)
---
HTTP/1.1 400 Bad Request
Content-Type: text/html; charset=us-ascii
Server: Microsoft-HTTPAPI/2.0
Date: Thu, 07 Aug 2014 08:52:28 GMT
Connection: close
Content-Length: 334
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN""http://www.w3.org/TR/html4/strict.dtd">
<HTML><HEAD><TITLE>Bad Request</TITLE>
<META HTTP-EQUIV="Content-Type" Content="text/html; charset=us-ascii"></HEAD>
<BODY><h2>Bad Request - Invalid Hostname</h2>
<hr><p>HTTP Error 400. The request hostname is invalid.</p>
</BODY></HTML>
read:errno=0
And (TLS 1.0 with SNI):
$ echo -e "GET / HTTP/1.1\n" | openssl s_client -connect example.com:443 \
-tls1 -servername example.com -ign_eof -CAfile Equifax_Secure_Certificate_Authority.pem
CONNECTED(00000003)
...
Start Time: 1407401898
Timeout : 7200 (sec)
Verify return code: 0 (ok)
---
HTTP/1.1 400 Bad Request
Content-Type: text/html; charset=us-ascii
Server: Microsoft-HTTPAPI/2.0
Date: Thu, 07 Aug 2014 08:57:55 GMT
Connection: close
Content-Length: 334
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN""http://www.w3.org/TR/html4/strict.dtd">
<HTML><HEAD><TITLE>Bad Request</TITLE>
<META HTTP-EQUIV="Content-Type" Content="text/html; charset=us-ascii"></HEAD>
<BODY><h2>Bad Request - Invalid Hostname</h2>
<hr><p>HTTP Error 400. The request hostname is invalid.</p>
</BODY></HTML>
read:errno=0
It does not appear to be Server Name Indication (SNI) related. I'm not sure SNI being honored at this point. Is this IIS 7.5 or below? IIS 8 provides SNI, and that might help the issue since the request will be routed immediately to the correct virtual domain in IIS.
Next, add a host header:
$ echo -e "GET / HTTP/1.1\nHost:example.com\n" | openssl s_client -connect example.com:443 \
-ssl3 -ign_eof -CAfile Equifax_Secure_Certificate_Authority.pem
CONNECTED(00000003)
...
Start Time: 1407402117
Timeout : 7200 (sec)
Verify return code: 0 (ok)
---
read R BLOCK
HTTP/1.1 302 Found
Cache-Control: private
Transfer-Encoding: chunked
Content-Type: text/html; charset=utf-8
Location: /Login/Login
Server: Microsoft-IIS/7.5
Set-Cookie: ASP.NET_SessionId=310xiuzver13lqoau0il0tsu; path=/; HttpOnly
X-AspNetMvc-Version: 3.0
X-AspNet-Version: 4.0.30319
X-Powered-By: ASP.NET
Date: Thu, 07 Aug 2014 09:01:34 GMT
The 302 redirect looks wrong. Shouldn't that be a 301? See HTTP redirect: 301 (permanent) vs. 302 (temporary). Also check out How can I make Chrome stop caching redirects? and the "won't fix" bug.
For completeness, here's the result following the redirect to /Login/Login:
$ echo -e "GET /Login/Login HTTP/1.1\nHost:example.com\n" | openssl s_client -connect example.com:443 \
-ssl3 -ign_eof -CAfile Equifax_Secure_Certificate_Authority.pem
CONNECTED(00000003)
...
Start Time: 1407403671
Timeout : 7200 (sec)
Verify return code: 0 (ok)
read R BLOCK
HTTP/1.1 200 OK
Cache-Control: private
Content-Type: text/html; charset=utf-8
Server: Microsoft-IIS/7.5
X-AspNetMvc-Version: 3.0
X-AspNet-Version: 4.0.30319
X-Powered-By: ASP.NET
Date: Thu, 07 Aug 2014 09:27:29 GMT
Content-Length: 1547
<html>
<body>
<form action="/Login/Login" method="post"> <div style="height: 140px">
</div>
<table style="width: 400px; border: 1px solid #058fbe;" cellpadding="5" align="center">
<tr>
<td colspan="2" align="center" style="background-color: #058fbe">
<span style="color: #FFF; font-family: Arial, Helvetica, sans-serif;
font-weight: bold; font-size: 14pt">TERRANET. ZONA ADMINISTRACIÓN</span>
</td>
</tr>
<tr>
<td width="150px">
<img src="/Content/img/login.png" width="150px" />
</td>
<td>
<span style="color: #058fbe; font-family: Arial, Helvetica, sans-serif;
font-weight: bold; font-size: 10pt">usuario</span><br />
<input type="text" style="border: 1px solid #058fbe; width: 190px" name="usuario" /><br />
<span style="color: #058fbe; font-family: Arial, Helvetica, sans-serif;
font-weight: bold; font-size: 10pt">contraseña</span><br />
<input type="password" style="border: 1px solid #058fbe; width: 190px" name="pass" /><br />
<br />
<input type="submit" value="entrar" style="background-color: #058fbe;
width: 80px; color: white; font-family: Arial, Helvetica, sans-serif;
font-weight: bold; font-size: 10pt; border: none" />
</td>
</tr>
</table>
</form>
</body>
</html>
EDIT (August 7, 2014): I see your changes of HTTP/1.1 301 Moved Permanently.
I performed some browsers tests today. I used:
- Chrome (Mac Book)
- Firefox (Mac Book)
- Safari (Mac Book).
- Mobile Browser (Android)
- Mobile Chrome (iPhone)
- Mobile Safari (iPhone)
- Explorer (Surface Pro)
Most worked as expected.
Explorer on the Surface Pro tablet hung.
Android's browser (com.android.browser) prompted for a client cert (that's why I am being prompted to set a PIN):
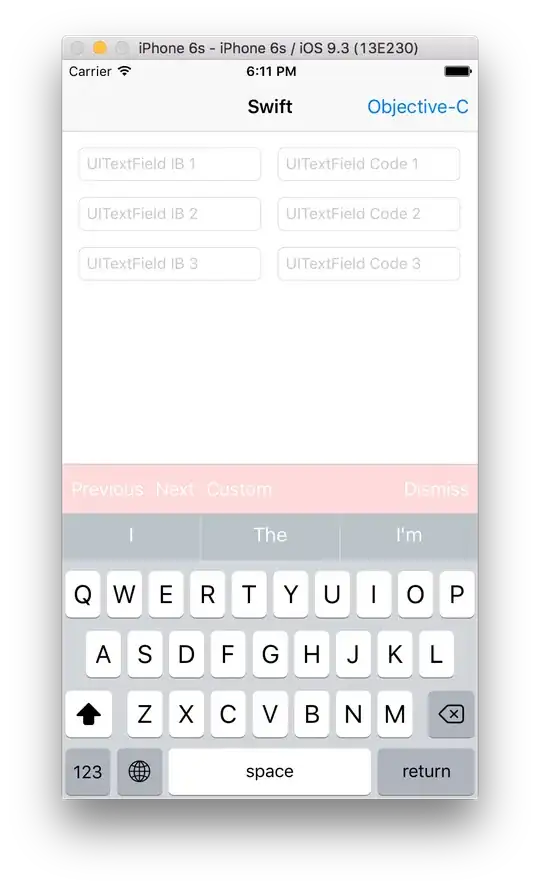
Safari desktop prompted for a client cert:
Do you need client certificates? If so, that's probably the issue. Client side certificates are a mess in browsers.
If you don't need them, then disable them in IIS. See Specify Whether to Use Client Certificates (IIS 7).

