Some days ago I connected a USB contact-less Smart-Card reader and sniffed that USB port via an USB Sniffer tool. Afterward, I put a 1k Mifare card on the reader and read 1 byte.
I take a look at the sniffer tool output and understand that the keys (read key and write key) transferred to the card without any encryption!
Now I want to know is this mechanism really safe??! If I change my reader's API to make it behave like a Mifare card and move it close to the original reader and sniff the communication between two card readers via my computer can't I gain the keys?!
Is this possible to make a Reader behave like a mifare card in the field of another contactless reader?
Update :
As I know it is mandatory to load keys on mifare card, before sending authenticate command!
As you see below, I load keys on card! [It is FF FF FF FF FF FF by default].

Simultaneously I sniffed the USB port that my ACRA122U connected to! As you see below, the keys was sent in plain!
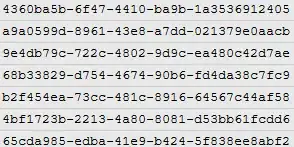
What is wrong with what I did?!
Note: Miss Hedayat (My Colleage), also confirmed it! :))