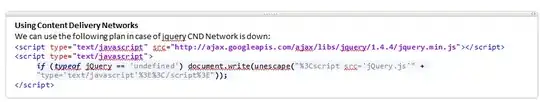
My problem is simple, only look the screenshot:
**For tired eyes:
-bash-4.1$ cat /etc/*release
LSB_VERSION=base-4.0-amd64:base-4.0-noarch:core-4.0-amd64:core-4.0-noarch:graphics-4.0-amd64:graphics-4.0-noarch:printing-4.0-amd64:printing-4.0-noarch
Red Hat Enterprise Linux Server release 6.6 (Santiago)
Red Hat Enterprise Linux Server release 6.6 (Santiago)
-bash-4.1$
-bash-4.1$
-bash-4.1$ elinks -version
ELinks 0.12pre5
Built on Jan 4 2013 07:04:04
Features:
Standard, IPv6, gzip, bzip2, UTF-8, Periodic Saving, Viewer (Search
History, Timer, Marks), Cascading Style Sheets, Protocol
(Authentication, BitTorrent, File, FTP, HTTP, URI rewrite, User
protocols), SSL (OpenSSL), MIME (Option system, Mailcap, Mimetypes
files), LED indicators, Bookmarks, Cookies, Form History, Global
History, Goto URL History
-bash-4.1$
-bash-4.1$
-bash-4.1$ elinks -dump -eval 'set connection.ssl.cert_verify = 1' https://10.113.1.104:443/sgc/registro2.asp
ELinks: SSL error
-bash-4.1$
-bash-4.1$
-bash-4.1$ elinks -dump -eval 'set connection.ssl.cert_verify = 0' https://10.113.1.104:443/sgc/registro2.asp
ELinks: SSL error
-bash-4.1$
I don't understand why elinks still shows the error SSL. Any idea?