When building an OAuth 2 server, is there anything wrong with associating scopes to users? Essentially allowing scopes to act as your applications roles?
I've looked at the RFC but can't seem to find any guidance on this.
The use case for a flow would be something like this:
A client requests an access token.
|
↓
On the server side: it checks to see if the user
is able to receive the requested scope(s).
⁄ \
↙ ↘
Check Passes: Check Fails:
| |
↓ ↓
Server issues token. Server denies request for token.
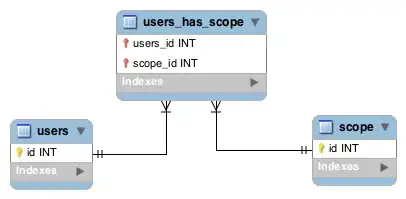
Some more visual context, this is a SQL data representation: