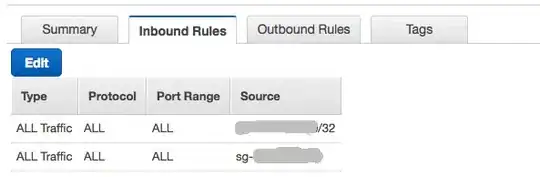
I created an AWS Lambda function that:
- logs onto Redshift via JDBC URL
- runs a query
Locally, using Node, I can successfully connect to the Redshift instance via JDBC, and execute a query.
var conString = "postgresql://USER_NAME:PASSWORD@JDBC_URL”;
var client = new pg.Client(conString);
client.connect(function(err) {
if(err) {
console.log('could not connect to redshift', err);
}
// omitted due to above error
However, when I execute the function on AWS Lambda (where it's wrapped in a async#waterfall block), AWS Cloudwatch logs tells me that the AWS Lambda function timed out after 60 seconds.
Any ideas on why my function is not able to connect?