i've been google'ing the difference between digital signature and digital certificate (asymmetric encryption) seems like they are the same. I would like to clarify if they are the same or not? many thanks!!!
10 Answers
A digital signature is used to verify a message. It is basically an encrypted hash (encrypted by the private key of the sender) of the message. The recipient can check if the message was tampered with by hashing the received message and comparing this value with the decrypted signature.
To decrypt the signature, the corresponding public key is required. A digital certificate is used to bind public keys to persons or other entities. If there were no certificates, the signature could be easily be forged, as the recipient could not check if the public key belongs to the sender.
The certificate itself is signed by a trusted third party, a Certificate Authority like VeriSign.
Let me expand of Ashley's explanation. As with all things crypto, assume Alice (sender) wants to send a secure message to Bob (recipient)
There are two problem to solve here.
- How to encrypt the message so only Bob can decrypt it.
- How can Bob be sure the message is from Alice in the first place and not modified by someone in transit.
Both of these problems can be solved with public key cryptography. For (1), Alice encrypts the message with Bob's public key. When bob receives the message, he can securely decrypt it with his private key. So encrypt with Bob's public key and decrypt with Bob's private key (this is basic stuff in public key crypto)
To solve (2), Alice also sends a digital signature along with the encrypted message. This is done as follows:
- Pass the original message through a hash function (like sha-1) to get a message digest
- Encrypt this message digest with Alice's private key (note this is the opposite of how the original message is encrypted with Bob's public key)
When Bob receives the message + digital signature he will:
- Decrypt the message with this private key and then calculate its message digest. Lets call this digest M1.
- Decrypt the signature with Alice's public key to get the message digest. Lets call this M2.
- If M1 and M2 are same, Bob can be certain that the message was not modified in transit and that indeed it is from Alice.
As for digital certificates, notice that Alice relies on encrypting the original message with Bob's public key and Bob relies on Alice's public key to decrypt the signature. How can both of them be sure of each other's public key? Thats what digital certificates are for. Its allows a trusted third party to verify/say "Alice's public key is xyz".
- 19,394
- 9
- 63
- 66
-
@numan If I have a website, how can CA verify that it's my website sending the public key ?(during the digital certificate verification)? – Prajwal Feb 09 '19 at 18:13
-
1Great Explanation ! – Snake Apr 19 '19 at 22:12
-
@numan When Bob receives the message + digital signature he will: Decrypt the message with this private key and then calculate its message digest. Lets call this digest M1: --> What is this 'private key'? Or where is it coming from? Bob's or Alices? I am confused as Bob had just received a message and now we are referencing 'this' private key.... – RobRen Feb 10 '20 at 17:08
-
@RobRen, Each party has its own private key. That's why the key is called _private_. So, to answer your question, Bob always decrypts messages using his own private key. Probably, numan made a typo and it should've been written **his** private key, not this private key. – Stan Mots Jun 08 '20 at 17:51
The clearest explanation for me is available at RSA Laboratories:
Digital signature: Suppose Alice wants to send a signed document or message to Bob. The first step is generally to apply a hash function to the message, creating what is called a message digest. The message digest is usually considerably shorter than the original message. In fact, the job of the hash function is to take a message of arbitrary length and shrink it down to a fixed length. To create a digital signature, one usually signs (encrypts) the message digest as opposed to the message itself.
...
Alice sends Bob the encrypted message digest and the message, which she may or may not encrypt. In order for Bob to authenticate the signature he must apply the same hash function as Alice to the message she sent him, decrypt the encrypted message digest using Alice's public key and compare the two. If the two are the same he has successfully authenticated the signature. If the two do not match there are a few possible explanations. Either someone is trying to impersonate Alice, the message itself has been altered since Alice signed it or an error occurred during transmission.
...
Digital certificate: In addition, someone could pretend to be Alice and sign documents with a key pair he claims is Alice's. To avoid scenarios such as this, there are digital documents called certificates that associate a person with a specific public key.
These quotes are from RSA labs at http://www.rsa.com/rsalabs/node.asp?id=2182 and http://www.rsa.com/rsalabs/node.asp?id=2277
- 60,973
- 31
- 151
- 169
From Wikipedia (emphases mine):
A digital signature or digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, and that it was not altered in transit. Digital signatures are commonly used for software distribution, financial transactions, and in other cases where it is important to detect forgery and tampering.
and
In cryptography, a public key certificate (also known as a digital certificate or identity certificate) is an electronic document which uses a digital signature to bind together a public key with an identity — information such as the name of a person or an organization, their address, and so forth. The certificate can be used to verify that a public key belongs to an individual.
So if I understand the above correctly, a digital signature just proves that a document hasn't been tampered with whereas a digital certificate proves that the document actually came from you.
- 5,482
- 3
- 36
- 44
- 19,581
- 6
- 68
- 84
Conceptually they are kind of oposites. With a digital certificate encypt you with the public key and decrypt with the private key, that way you can ensure only the person with the private key can read your text. With a digital signature you encrypt with the private key and decrypt with the public key, that way anyone can decrypt, but only the person with the private key can encrypt so you know the message has come from the person with the private key.
- 21,601
- 5
- 62
- 79
-
Seems to me that you can also sign a message with the private key of a certificate and someone can verify the message with the public key of the certificate – Kias Dec 03 '15 at 07:10
-
2This is a really horrible explanation. It is completly handwavy - something that should be avoided as far as possible in security topics. It doesn't make clear *who* encrypts/decrypts *what* (We are not encrypting messages in any of the two concepts!). Moreover the explanation for the digital certificate is just plain wrong - I recommend reading the other answers or any other source. I wonder how this answer got any upvotes. – dingalapadum May 14 '18 at 09:32
Digital signature explained:
Sender : Encrypt(hash(message), priv_key) = dig_sign
Receiver : Decrypt(dig_sign, pub_key) => hash_of_message == hash(message)
- 2,875
- 4
- 28
- 46
@numan's answer provides a good explanation of the necessary process to ensure confidentiality, integrity, and authentication. But this doesn't answer a real question.
The goal of a Digital Signature is to provide these basic services,
Authenticity: Sender has signed the data as he claimed (Data have to be encrypted using sender's private key).
Integrity: To provide a guarantee that the data has not changed from the time it was signed.
Nonrepudiation: The receiver can provide the data to some third party which can accept the digital signature as proof that the data exchange did take place. Besides, the sender (signing party) cannot refuse that it has signed the data.
and it has properties to ensure authenticity and integrity, such as,
The signature is not forgeable: Provides proof that the signer, and no one else, signed the document.
Signature cannot be repudiated: which means, for legal purposes, the signature and the document are considered physical things. Signers cannot claim later that they did not sign it.
Signature is unaltered: After a document is signed, it cannot be altered.
Signature is not reusable: The signature is part of the document and cannot be moved to a different document.
While on the other hand, a Digital certificate is issued by some third-party Certificate Authority (CA) to verify the identity of the certificate holder. It actually contains Certification authority's digital signature that is derived from CA's own private key.
It also contains the public key that is associated with the owner of the digital certificate.
You may want to read about how Digital Certificates are strucutred.
- 18,164
- 14
- 82
- 110
Digital Signatures are generated electronically, which is used to ensure the authenticity & integrity of data for example e-mail message. Whereas, Digital Certificate is a medium to prove the identity of website holder and it gives the protection against data exchange from visitors to the sender.
It can be said that it's similar to other identity proofs of a person like driver's license or any employee ID card. Trusted third parties issues digital certificates, for establishing the identity of the person who owns certificate. These third parties who issues digital certificates are known as Certificate Authority (CA). In simple words, Digital Certificates are used to do verification of the trustworthiness of a website and Digital Signatures are used to verify the trustworthiness of the information.
Generally, three algorithms are used by a digital signature system. First - Key generation algorithm is used to generate a public and private key pairs. Second - Signing algorithm is used to generate a signature which is used at time of giving out private key and a message. Third and lastly, signature verifying algorithm is used for the verification of the message, a signature & the public key. Here’s the common reasons for applying a Digital Signature.
1.Authentication
2.Integrity
3.Non-repudiation
Whereas Digital Certificates, uses a digital signature for attaching a public key with any particular entity or individual. Some of the information carried along with digital certificates are like, a serial number which is used to identify every certificate uniquely, the individual or entity identified by the certificate and the algorithm which is used for creating the signature. Apart from this, it contains the CA which verifies all the information of the certificate, validation and expiry date of the certificate. It also contains public key and thumbprint to assure that certificate is not modified. Digital Certificates are mostly used on E-commerce websites which are based on HTTPS to gain trust of the website visitors.
Digital Certificate contains the following things:
Certificate Holder Name
Serial Number
Certificate Expiry Date
Copy of Certificate Holder’s Public Key
Digital Signature of Certificate Authority
Key Difference of Digital Signature & Digital Certificate
Digital Signature
It verifies the authenticity of a document
Asymmetric keys are used to encrypt and decrypt the document.
It offers authentication, non-repudiation and integrity.
Digital Certificate
It creates an identity & improves the trustworthiness of websites.
A certificate is issued by a certificate authority after the verification process completes.
Read details about digital signatures and how they work and about digital certificates here.
- 400
- 3
- 10
I'm recently researching something about digital signature and digital certificate and found a interesting blog, based on the fact that the web page might be broken, let me try to illustrate it here.
Firstly, let's go through Public-key cryptography on wiki,
Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys which may be disseminated widely, and private keys which are known only to the owner. The generation of such keys depends on cryptographic algorithms based on mathematical problems to produce one-way functions. Effective security only requires keeping the private key private; the public key can be openly distributed without compromising security.
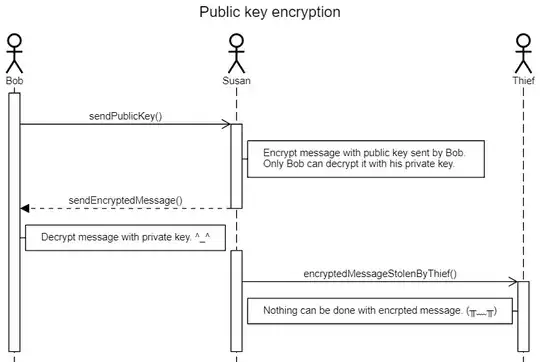
One common usage of Public-key cryptography is Public key encryption, I summarized the common usage scenario with sequence diagram below:
Bob has public key and private key, he can give public key to multiple message senders. For those sender, they can use public key to encrypt the message before sending it. Only Bob can decrypt the message with private key. For other receiver, they don't know what's real message is.
Another common usage of Public-key cryptography is Digital signatures, please check the diagram as below:
On the contrary, Bob uses private key to encrypt digest to signature. Pat knows that the document is sent by Bob if he can decrypt the signature with provided public key. By hash received document to digest, he can then check whether the document has been modified or not by comparing it to decrypted digest.
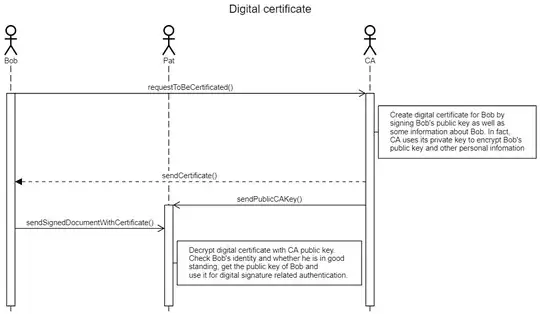
However, assume there is somebody named Doug who pretends to be Bob and wants to deceive Pat. He can send public key and digital signature to Pat in the name of Bob, how can Pat know whether the key is from Bob or not? That's why digital certificate is imported.
Let's check diagram below:
The Certificate Authority acts as trusted third party. It means the digital certificate is issued by CA if it can be decrypted by CA public key. After decryption, pat will check whether Bob is in good standing and the certificate information about Bob's identity has not been altered. Pat then takes Bob's public key to do digital signature related authentication as mentioned above.
- 10,627
- 5
- 49
- 67
No difference if signature / certificate is signed by the same CA / trusted entity.
If the signed data contains some signed data (e.g. public key of the sender) signed by CA / trusted entity to entrust the sender (i.e. chain of trust), there is no difference as well (or we should call the signed data certificate?).
In other words, certificate is a kind of usages of signature.
- 446
- 6
- 5
-
3This is **not true** for the common lingo used for signatures and certificates in the context of X509 PKIs which usually are meant in such questions. – mkl Jul 31 '15 at 04:12