Predictable IVs can be exploited by chosen plain text.
Pretend that Eve is a DBA at an insurance company. The company collects medical histories from beneficiaries that include a lot of true/false check boxes about medical conditions. This company also happens to its own health insurance provider. Eve realizes that Alice could be blackmailed if she can discover that Alice has a particularly embarrassing medical condition. However, the value in each of these fields is encrypted, so even though Eve is the DBA, she only has access to the cipher text.
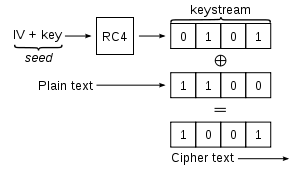
In CBC, the IV is XORed (noted by "⊕" below) with the plain text, then run through the block cipher: C1 = Ek(IV ⊕ P1).
Since Eve is a beneficiary of the insurance company, she can choose the plain text for her own medical record, and since she is the DBA, she can examine anyone's cipher text. In addition to using predictable IVs, the sloppy application developer did a poor job of validating the application inputs. If Eve can predict the IVs that will be applied to her (IVeve) and Alice's (IValice) records in advance, she can choose the plain text for her own record like this: Peve = IVeve ⊕ IValice ⊕ "false"
The application encrypts this plain text like this:
Ceve = Ek(IVeve ⊕ Peve) = Ek(IVeve ⊕ (IVeve ⊕ IValice ⊕ "false"))
The IVeve ⊕ IVeve cancels out, which means that Ceve = Ek(IValice ⊕ "false")
Now Eve can compare Ceve and Calice. If they are different, she knows that Alice must have entered "true" for that medical condition.
Making IVs unpredictable thwarts this attack, and an easy way to make them unpredictable is to choose them randomly after the plain text has been supplied.