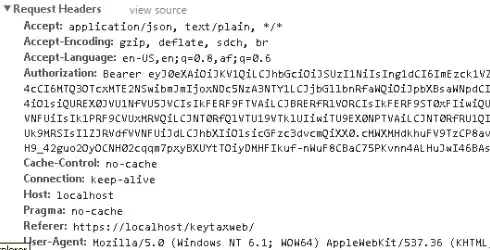
I did a project a while ago using oAuth2 and OpenID for access control and I managed to get it working nicely, but now I started on a new project and I have to implement token validation again. I used the same patterns, settings, configuration and technology as the previous project (90% of the settings are the same) and my tokens are populated correctly and passed to my API as a header with the HTTP requests:
Old
Translated: { "iss": "https://localhost", "aud": "https://localhost/resources", "exp": 1479710870, "nbf": 1479707270, "client_id": "implicit", "scope": [ "openid", "profile", "roles", "web" ], "sub": "55dad807b33c2c2648342757", "auth_time": 1479705621, "idp": "idsrv", "role": "Administrator", "function": [ "form-view", "form-add", "... etc" ], "amr": [ "password" ] }
New
Translated: { "iss": "https://localhost", "aud": "https://localhost/resources", "exp": 1479711165, "nbf": 1479707565, "client_id": "implicit", "scope": [ "openid", "profile", "roles", "web" ], "sub": "SYSTEM", "auth_time": 1479707564, "idp": "idsrv", "role": "System user", "function": [ "ADD_BUSS_UNIT", "ADD_EMP", "... etc" ], "amr": [ "password" ] }
(The Cache-control is extra on the new project, could that be causing the problem? Seems unlikely?)
Anyway, for some reason when I get to the controller, the HttpContext.Current.User.Identity is populated as System.Security.Principal.WindowsIdentity instead of the ClaimsIdentity that I expect to see:
Old
New
The biggest difference between the two projects is that the new one is running in Windows Server 2008 R2 and the old one is running on Windows7. The IIS versions are the same and the setup in IIS is also the same and as I mentioned, most of the other setttings are the same.
My Startup Class for the API:
public void Configuration(IAppBuilder app)
{
// Allow all origins
app.UseCors(CorsOptions.AllowAll);
JwtSecurityTokenHandler.InboundClaimTypeMap = new Dictionary<string, string>();
System.Net.ServicePointManager.ServerCertificateValidationCallback = delegate { return true; };
app.UseIdentityServerBearerTokenAuthentication(
new IdentityServerBearerTokenAuthenticationOptions
{
Authority = Constants.STSAuthEndPoint,
RoleClaimType = "role",
RequiredScopes = new[] { "web" }
});
}
A couple of ideas from my side as to why it's not working:
- Impersonation - Could it be that IIS or Windows Server is impersonating a user? I checked the settings between the two servers and everything looks the same.
- The SUB value - I use the username on the new project and used a Guid format ID on the previous one. I remember seeing something about the sub value being a combination of two values, but I don't know if this could be causing the problem?
- Role - Could the space in the role name be causing an issue?
- Login screen - I created a new login screen for the new project that is a lot more customised than the previous one, but the login works, the API just doesn't pick up that user.
I have LOTS of additional information that I can provide, but I don't want to make the post too long, so please let me know if more information is required.
I appreciate any help that can be provided.