So instead of https://s3.amazonaws.com/static.my-company.com/media/my-file.jpg, I want it to be addressed as https://static.my-company.com/media/my-file.jpg. How can I do that?
There are three separate issues, here.
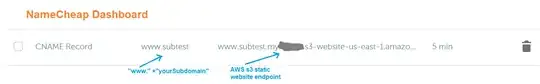
If you enable the web site hosting feature for your bucket, as @Deif illustrates in another answer here, you can point the hostname in Route 53 to the bucket's web site endpoint using an Alias or CNAME and it works. But it doesn't support HTTPS.
HTTPS requires that the web server identify itself to the browser with an SSL (TLS) certificate that includes a hostname matching the one in the browser's address box. The S3 certificates on the REST endpoint match various permutations of s3.amazonaws.com -- they don't match your domain.
So you need an SSL certificate. If you already have one, upload it into Amazon Certificate Manager (ACM) in the us-east-1 region.¹ If not, ACM can create one for you for free.
Next, create a new CloudFront distribution, using your subdomain as an Alternate Domain Name, using the ACM certificate above, and using your web site endpoint hostname as the Origin Server.
Then, point your subdomain in Route 53 to the CloudFront distribution.
Now, https://subdomain.example.com/pics/funny/cat.jpg goes to CloudFront which provides SSL and fetches the content from the appropriate bucket.
Why is CloudFront necessary? That's the official solution for using a custom domain name with SSL enabled with S3. S3 doesn't support the capability natively. Using CloudFront has an accompanying cost, but it significantly reduces the cost of S3 itself. When a download occurs through CloudFront, S3 charges $0 for the bandwidth used for the download and CloudFront bills the bandwidth instead. The CloudFront price for bandwidth is lower in many cases (presumably because CloudFront can scale horizontally to alleviate congestion, while S3 can only scale vertically -- it is location constrained by design).
¹ In ACM, the us-east-1 region is always used for the setup I describe here, regardless of the bucket location because CloudFront is managed out of us-east-1 and we need this certificate to be accessible to CloudFront.