I was asked to set up HTTPS with a self-signed cert on Apache on localhost, but how do I actually do that? I have no idea at all.
-
2Use [Serveo](http://serveo.net)! `ssh -R youruniquesubdomain:80:localhost:3000 serveo.net` Slap in your subdomain and port number and you ready to go on [`https://youruniquesubdomain.serveo.net`](https://youruniquesubdomain.serveo.net) – totymedli Jul 11 '18 at 13:15
-
@totymedli I get ssh: connect to host serveo.net port 22: Connection refused – Timo Oct 21 '20 at 10:49
-
2@Timo Seems like Serveo is dead, but [localhost.run](https://localhost.run) does the same: `ssh -R 80:localhost:8080 ssh.localhost.run` – totymedli Oct 22 '20 at 11:59
-
@totymedli, awesome answer-comment! I had this going in a couple of minutes, didn't even read any of those verbose answers, lol. – Octopus Jan 21 '21 at 04:32
-
@totymedli how am I suppose to use this service...I do run the command in the windows terminal...but from there where to? – Dimitris Papageorgiou Mar 30 '22 at 12:54
-
@DimitrisPapageorgiou You open the link printed by the script. You can use it by yourself or send it to anybody over the internet and it will be an HTTPS connection to your local env. – totymedli Apr 01 '22 at 01:01
-
@totymedli well I did try that and I get ERR_EMPTY_RESPONSE....so sth is preventing the connection...I tried also on a different browser. – Dimitris Papageorgiou Apr 01 '22 at 02:37
-
Well...i changed localhost to 127.0.0.1....changed the port from 8080 to 80 and it worked – Dimitris Papageorgiou Apr 01 '22 at 03:39
16 Answers
I've just attempted this - I needed to test some development code on my localhost Apache on Windows. This was WAAAY more difficult than it should be. But here are the steps that managed to work after much hairpulling...
I found that my Apache install comes with openssl.exe which is helpful. If you don't have a copy, you'll need to download it. My copy was in Apache2\bin folder which is how I reference it below.
Steps:
- Ensure you have write permissions to your Apache conf folder
- Open a command prompt in
Apache2\conffolder - Type
..\bin\openssl req -config openssl.cnf -new -out blarg.csr -keyout blarg.pem You can leave all questions blank except:
- PEM Passphrase: a temporary password such as "password"
- Common Name: the hostname of your server
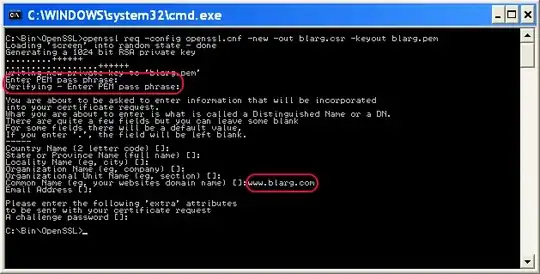
When that completes, type
..\bin\openssl rsa -in blarg.pem -out blarg.keyGenerate your self-signed certificate by typing:
..\bin\openssl x509 -in blarg.csr -out blarg.cert -req -signkey blarg.key -days 365
Open Apache's
conf\httpd.conffile and ensure SSL module is enabled - there should be no hash at the start of this line:
LoadModule ssl_module modules/mod_ssl.so
Some Apache installations place the SSL config in a separate file. If so, ensure that the SSL conf file is being included. In my case I had to uncomment this line:
Include conf/extra/httpd-ssl.confIn the SSL config
httpd-ssl.confI had to update the following lines:- Update
SSLSessionCache "shmcb:C:\Program Files (x86)\Zend\Apache2/logs/ssl_scache(512000)"
to
SSLSessionCache "shmcb:C:/Progra\~2/Zend/Apache2/logs/ssl_scache(512000)"
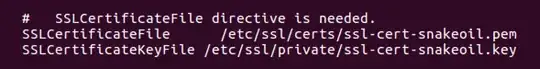
(The brackets in the path confuse the module, so we need to escape them) DocumentRoot- set this to the folder for your web filesServerName- the server's hostnameSSLCertificateFile "conf/blarg.cert"SSLCertificateKeyFile "conf/blarg.key"
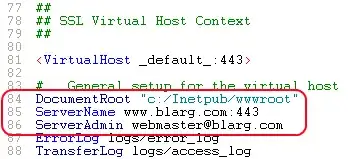
- Update
Restart Apache.
- Try loading
https://localhost/in your browser.
Hopefully you made it this far. Feel free to update this post with any other helpful info.
(Screenshots courtesy of Neil Obremski and his helpful article - although now quite out-of-date.)
- 55,742
- 17
- 139
- 133
-
2Thanks. I also had to edit the ErrorLog, TransferLog and CustomLog directives to valid paths otherwise Apache wouldn't start. – Tamlyn Nov 29 '12 at 17:32
-
Thanks. Instructions worked like a charm. Though I had to create a symlink to Apache directory get rid of brackets in path "C:\Program Files (x86)\Apache Software Foundation\Apache2.2". More instructions here: http://jamesmcdonald.id.au/it-tips/32-bit-apache-on-windows-error – Hermann Feb 01 '13 at 10:44
-
1
-
Hi @Jacobian. At which step did you get stuck? Was there an error message? Maybe we can help. – Simon East Dec 04 '14 at 01:23
-
I get this error right at the third step - just a bunch of error messages im my console – Jacobian Dec 05 '14 at 06:44
-
@Jacobian In order to fix those errors you have to place a copy of `openssl.cnf` (which is located at `C:\xampp\apache\conf on Windows`) in your xampp root folder (`C:\xampp` or your equivalent). – D. Visser Jun 08 '15 at 19:44
-
I can properly configure using these instructions, but i get a 403 forbidden when I try to access the host. no configuration errors when i restart apache... – FlavorScape Dec 09 '15 at 18:46
-
@FlavorScape if you're getting a 403, it might be because you're missing a `
` block with the necessary permissions or some other IP or security rule is in place. – Simon East Dec 10 '15 at 01:44 -
8I had to uncomment the following as well in my httpd.conf for it to work: LoadModule socache_shmcb_module modules/mod_socache_shmcb.so – erik Sep 21 '16 at 11:33
-
1I did two more steps to make it work, add module LoadModule socache_shmcb_module modules/mod_socache_shmcb.so and in httpd-ssl.conf I correct ssl log path at line 250, CustomLog ".apache24/logs/ssl_request.log" \ – Wasim A. Nov 28 '16 at 13:47
-
5In order to generate the .pem and .key files, I had to set 2 environment variables at step 2 : set OPENSSL_CONF=C:\path\to\apache\Apache2.4.4\conf\openssl.cnf set RANDFILE=C:\path\to\apache\Apache2.4.4\conf\.rnd – eosphere Apr 09 '17 at 11:27
-
The screenshots are for running openssl out of `c:\bin\ssl`. When I use the command in #3 `..\bin\openssl req -config openssl.cnf -new -out blarg.csr -keyout blarg.pem` the console shows a `WARNING: can't open config file: c:/openssl-1.0.2p-win64/ssl/openssl.cnf` -- is that a critical warning ? – Richard Jan 26 '19 at 12:21
-
warning: -- I have successfully setuped https with self signed certificate to my localhost after spending so may hours but then it all went waste because localhost dosen't support cookies which my site relies upon. so, be aware of it – Ajithkumar_sekar Jul 02 '19 at 12:17
-
mod_socache_shmcb just uncommnted that in httpd.conf, you saved my ages, thanks dude you rock – Aadam Oct 07 '19 at 14:50
-
These are pretty good instructions. I add some additional insights in case you follow these instructions and still can't get it to work. These instructions create a 509v1 type certificate. This will not work when accessing Apache Httpd with the new Chromium base Edge browser. You need to create a 509v3 type certificate and add the Extended Key Usage serverAuth and clientAuth. (Microsoft calls it an Enhanced Key Usage, but it the same thing) There's no problem generating one using openssl, it just takes some additional configuration and a additional parameter in the openssl command. – Tom Rutchik May 06 '20 at 21:09
-
In httpd.conf I needed to change the Directory directives to AllowOverride All Require all granted – John Aug 10 '22 at 08:32
I use ngrok (https://ngrok.com/) for this. ngrok is a command line tool and create a tunnel for localhost. It creates both http and https connection. After downloading it, following command needs to be run :
ngrok http 80
( In version 2, the syntax is : ngrok http 80 . In version 2, any port can be tunneled. )
After few seconds, it will give two urls :
http://a_hexadecimal_number.ngrok.com
https://a_hexadecimal_number.ngrok.com
Now, both the urls point to the localhost.
-
1@sudip, Does the opensource code of ngrok works in such a way that we can host this on our own server without modification? If not, it's pretty much a showstopper because it's **not ok** to redirect users requests to an external host like ngrok. – Pacerier Mar 15 '15 at 18:38
-
2@Pacerier I dont intend to use it on server. I use it on localhost (Bcz my network provider gives me a dynamic IP). I used it first time for paypal IPN testing and it worked perfectly. I wonder why someone will use it on server and for what purpose. – sudip Mar 16 '15 at 21:53
-
@sudip, The purpose is obvious, To allow code that works on HTTP to also work with HTTPS with no extra coding needed. – Pacerier Mar 19 '15 at 15:10
-
4Though this is useful, it seems incredibly insecure to allow access to your dev machine to the open internet. Using something like this would get you fired at a security conscious employer. – Andy M Apr 05 '16 at 14:47
-
@YumYumYum . It was completely free before in V 1. But, http and https ports are still free in v 2 ( dont know whether any port restriction is there is free plan ). Check the free plan here : https://ngrok.com/product#pricing – sudip Apr 15 '16 at 17:32
-
@AndyM . I agree. But, I use it mostly on localhost and specially to test paypal IPN notification .. – sudip Apr 15 '16 at 17:35
here is simplest way to do this
first copy these server.crt & server.key files (find in attachment ) into your apache/conf/ssl directory
then open httpd.conf file & add following line
Listen 80
Listen 443
NameVirtualHost *:80
NameVirtualHost *:443
<VirtualHost *:443>
DocumentRoot "d:/wamp/www" #your wamp www root dir
ServerName localhost
SSLEngine on
SSLCertificateFile "d:/wamp/bin/apache/Apache2.4.4/conf/ssl/server.crt"
SSLCertificateKeyFile "d:/wamp/bin/apache/Apache2.4.4/conf/ssl/server.key"
</VirtualHost>
- 2,329
- 4
- 24
- 30
-
3I had to enable also the module LoadModule ssl_module libexec/apache2/mod_ssl.so in the (/etc/apache2/httpd.conf) – Alexey May 08 '15 at 09:25
-
19I wonder how safe/dangerous is downloading *.crt *.key files from untrusted source instead of generating your own. – Petr Peller Apr 12 '16 at 16:22
-
6@PetrPeller we are setting up https for local development so why wonder for safe/dangerous – Anil Gupta Apr 13 '16 at 07:59
-
@AnilGupta By dangerous I meant that crt/key could contain malicious code to infect our local machines ... Maybe I am just being paranoid :) – Petr Peller Apr 13 '16 at 21:08
-
1@AnilGupta the files you have linked are no longer available.. will it be possible to rehost it somewhere else? – supersan Jan 19 '17 at 05:09
-
7An explanation how to generate those files would be great. Because downloading files from an unknown source is a bad practise, but also because that kind of links will break at some point. – Stephan Vierkant Apr 10 '17 at 19:28
-
1@AnilGupta: ignore others. just put the `.crt , .key` files in `gist.github.com`. So that brave guys like us can quickly make it up and running first before doing all alone and waste time. – Aug 31 '17 at 08:53
-
@YumYumYum (the brave guy) lolzz, i have linked files to gist.github.com as you suggested – Anil Gupta Dec 07 '17 at 09:32
-
I found a simple way to generate .crt and .key https://gist.github.com/nrollr/4daba07c67adcb30693e – Jyoti Duhan Jan 30 '18 at 08:20
-
2This tutorial is fine https://www.digitalocean.com/community/tutorials/how-to-create-a-ssl-certificate-on-apache-for-ubuntu-14-04 – Dhiraj Feb 09 '18 at 12:45
-
-
When I try to restart apache service I get this message in event viewer...NameVirtualHost has no effect and will be removed in the next release ....as a result the service cannot be restarted – Dimitris Papageorgiou Oct 14 '22 at 07:18
In order to protect the security of information being sent to and from your web server, it's a good idea to enable encryption of the communication between clients and the server. This is often called SSL.
So let's set up HTTPS with a self-signed certificate on Apache2. I am going to list the steps which you should follow:
- Install apache2 web-server on your machine. For linux machine open the terminal and type
sudo apt-get install apache2
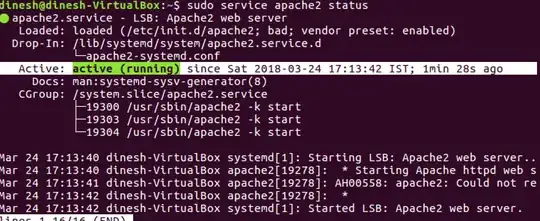
- After successful installation check the status of apache2 service by executing command
sudo service apache2 status
It should output
- Navigate to browser and type
http://localhost:80
Verify that you get default page for apache2 like this.
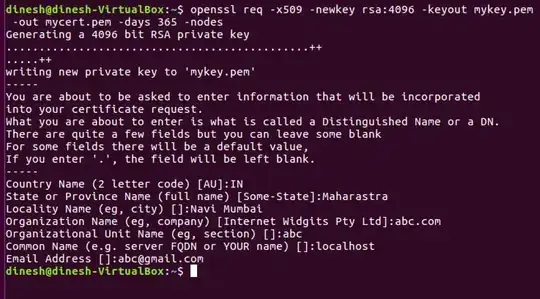
- For encrypting a web connection we need certificate from CA (certificate authority) or we can use self signed certificates. Let's create a self signed certificate using the following command.
openssl req -x509 -newkey rsa:2048 -keyout mykey.key -out mycert.pem -days 365 -nodes
Please fill the information accordingly as shown below.
mykey.key and mycert.pem should be created in your present working directory.
- It would be nice we if move certificates and keys at a common place and it will be easy for apache2 web server to find them. So let's execute the following commands
sudo cp mycert.pem /etc/ssl/certs
sudo cp mykey.key /etc/ssl/private
- Let's enable the SSL mode on your server
sudo a2enmod ssl
It should output like this
- Let's configure apache2 to use self signed certificate and key which we have generated above.
sudo vi /etc/apache2/sites-available/default-ssl.conf
Please find these two lines and replace them with your cert and key paths.
Initial
Final
- Enable the site
cd /etc/apache2/sites-available/
sudo a2ensite default-ssl.conf
- Restart the apache2 service
sudo service apache2 restart
- Verify the apache2 web-server on HTTPS. Open your browser again and type
https://localhost:443
It should output something like this with a warning that page you are about to view is not secure because we have configured the server with self-signed certificate.
- Congratulations you have configured your apache2 with HTTPS endpoint, now click on advanced --> add exception --> confirm security exception, you will see the default page again.
- 3,782
- 4
- 16
- 33
- 545
- 4
- 17
-
I prefer not to edit any config file if I can, so I left `default-ssl.conf` as it is. I was about to rename `mycert` to `ssl-cert-snakeoil` but this file already exists so I just used that! So I was able to safely skip two steps on Debian. – Rolf Jun 07 '18 at 09:09
-
@Rolf I agree with you but in production, it is always the case use a new certificate and key. So just to show how they can be created, I have added 2 additional steps for Debian. Thanks :) – Dinesh Kumar Jan 28 '20 at 12:08
-
Is there any way I can add my self-signed certificate as a certificate authority, to avoid seeing warnings? – Aaron Franke Jul 13 '20 at 01:13
Windows + Apache 2.4, for example:
uncomment ssl_module in your
httpd.conffile.LoadModule ssl_module modules/mod_ssl.solisten 443 port just like 80 port in your
httpd.conffile.Listen 80 Listen 443uncomment Include Virtual hosts in your
httpd.conffile.# Virtual hosts Include conf/extra/httpd-vhosts.confadd VirtualHost in your
conf/extra/httpd-vhosts.conf<VirtualHost _default_:443> DocumentRoot "D:/www" #your site directory path ServerName localhost #ServerAlias localhost.com localhost2.com SSLEngine on SSLCertificateFile "${SRVROOT}/conf/ssl/server.crt" SSLCertificateKeyFile "${SRVROOT}/conf/ssl/server.key" <Directory "D:/www"> Options -Indexes +FollowSymLinks +ExecCGI AllowOverride All Require all granted </Directory> </VirtualHost>
only the port number 443 and SSL...... lines are different from normal http config.
save you config file and restart apache service. then you can visit https://localhost/
The web browser will warn you that it's unsafe at the first time, just choose go on.
- 24,167
- 8
- 82
- 93
-
This has worked for me on XP Home, Apache 2.4. Copied the 2 certificate files from the previous post (by Anil Gupta). Uncommented mod_ssl and included httpd-vhosts.conf in httpd.conf, added Anil Gupta's VirtualHost directive (with some paths adjusted) in httpd-vhosts.conf. – jogi99 Apr 19 '16 at 09:36
It's actually quite easy, assuming you have an openssl installation handy. (What platform are you on?)
Assuming you're on linux/solaris/mac os/x, Van's Apache SSL/TLS mini-HOWTO has an excellent walkthrough that I won't reproduce here.
However, the executive summary is that you have to create a self-signed certificate. Since you're running apache for localhost presumably for development (i.e. not a public web server), you'll know that you can trust the self-signed certificate and can ignore the warnings that your browser will throw at you.
- 3,452
- 1
- 26
- 23
- 584
- 4
- 8
-
Hi, I'm working on Windows OS. And as for the self signed certificate, do I have to download it or by any other means? – KennC. Nov 19 '10 at 03:47
-
3Nope. You'll make the self-signed cert yourself. Do you have the apache httpd + ssl setup? You'll need the ssl in order to do this. This site: http://rubayathasan.com/tutorial/apache-ssl-on-windows/ has good info on getting ssl going on windows. You'll be doing some command-line work, but that's good for you anyway. :-) – Pete Clark Nov 19 '10 at 03:51
-
3
-
1Yeah - it does look to be dead. That's the internet for you... However, the link to the CentOS Wiki below referenced by @kayakinkoder is also good: https://wiki.centos.org/HowTos/Https If you're on a mac, this writeup also looks reasonable: https://gist.github.com/nrollr/4daba07c67adcb30693e – Pete Clark Jun 03 '17 at 02:58
-
Running Apache on Windows 10 here. I couldn't get Chrome to trust the certificate made in the top answer by Simon. What I ended up doing was using PowerShell to generate a self signed certificate.
Step 1 - Generate Self-Signed certificate
In PowerShell
New-SelfSignedCertificate -DnsName "localhost" -CertStoreLocation "cert:\LocalMachine\My" 1
Step 2 - Configure and Export Certificate
Type Certificate into the Windows search bar, click the Manage Computer Certificates control panel item that is suggested.
From the Certificate Management program that comes up (certlm), you should now see a localhost key under Personal >> Certificates.
I copied this certificate into Trusted Root Certification Authorities. I'll be honest in that I'm not sure if that's necessary.
Selecting the newly copied certificate, double click on it (the localhost certificate). From the Certificate modal, click the Details tab, then the Copy to File... button.
This will bring up and Export Wizard, I chose to export the private key, click next. I also chose to Export all extended properties (again, I'm not certain if that was necessary). I chose to use a simple password (pass) and the default encryption.
Choose a folder to export to and name the file. You can always move and rename the file if necessary. For simplicity's sake let's copy it to your conf folder under your Apache installation (In my case: C:\apache\conf) and name the file myCert (the resulting file will be a .pfx file)
Step 3 - Convert .pfx file for use with Apache
From here I basically followed the tutorial here, but I'll add instructions here (tweaked for our settings) in case that site goes down.
Open your Command Prompt in the /apache/conf/ folder
Run the following commands: Note: This assumes you have openssl.exe in the bin folder in the apache root folder (this should be standard/default)
..\bin\openssl pkcs12 -in myCert.pfx -nocerts -out privateKey.pem
This will prompt you for a password, enter what you input for Step 2 when you exported the .pfx file. In my case, this is pass. I entered the same password for the PEM phrase and again to verify. This will create a new file called privateKey.pem in your conf folder.
Then, run
..\bin\openssl rsa -in privateKey.pem -out private.pem
Again you will be prompted for a password (Enter pass phrase for privateKey.pem:), use the password you set for privateKey.pem. (In my case, pass)
You should see a message that says writing RSA key and a new file called private.pem in your conf/ folder. This will be your SSLCertificateKeyFile.
Now to generate the corresponding Server Certificate. Run:
..\bin\openssl pkcs12 -in myCert.pfx -clcerts -nokeys -out EntrustCert.pem
This will prompt you for a password, enter what you input for Step 2 when you exported the .pfx file. Enter it and you will now have a file called EntrustCert.pem in your conf folder. This is your SSLCertificateFile
Step 4 - Configure httpd.conf
Use the new files created as you server's key and certificate. Be sure to change your document root to where your files are!
ServerName localhost:80
Protocols h2 h2c http/1.1
<Directory />
Options FollowSymLinks
AllowOverride All
</Directory>
<VirtualHost _default_:443>
ServerName localhost:443
DocumentRoot ${SRVROOT}/htdocs/MYSITE
SSLEngine on
SSLCertificateFile "${SRVROOT}/conf/EntrustCert.pem"
SSLCertificateKeyFile "${SRVROOT}/conf/private.pem"
</VirtualHost>
Also in httpd.conf:
- Make sure
LoadModule ssl_module modules/mod_ssl.sois uncommented (no#in front) - Uncomment
LoadModule socache_shmcb_module modules/mod_socache_shmcb.so - Uncomment
LoadModule http2_module modules/mod_http2.so - Uncomment
Include conf/extra/httpd-ssl.conf(NOTE: Ensure that's where the file is!)
I also have curl and open ssl libraries included:
# load curl and open ssl libraries
LoadFile "C:\php\libeay32.dll"
LoadFile "C:\php\ssleay32.dll"
LoadFile "C:\php\libssh2.dll"
These modules shouldn't be necessary, but I'll note that I have them enabled:
LoadModule rewrite_module modules/mod_rewrite.so
LoadModule filter_module modules/mod_filter.so
LoadModule deflate_module modules/mod_deflate.so
Step 5 - Config httpd-ssl.conf
In the extra/ folder in the conf/ folder you should see a file called httpd-ssl.conf.
5a. Change the DocumentRoot -
Change the DocumentRoot from the default to the directory where your files are.
5b. Change the ServerName -
Change the ServerName from the default (something like www.example.com:443) to localhost:443
5c. Change the SSLCertificateFile
Change the SSLCertificateFile from the default (${SRVROOT}/conf/server.crt) to ${SRVROOT}/conf/EntrustCert.pem
5c. Change the SSLCertificateKeyFile
Change the SSLCertificateKeyFile from the default (${SRVROOT}/conf/server.key) to ${SRVROOT}/conf/private.pem
All together, in the <VirtualHost _default_:443> tag.
# General setup for the virtual host
DocumentRoot "${SRVROOT}/htdocs/MYSITE"
ServerName localhost:443
ServerAdmin admin@example.com
ErrorLog "${SRVROOT}/logs/error.log"
TransferLog "${SRVROOT}/logs/access.log"
# SSL Engine Switch:
# Enable/Disable SSL for this virtual host.
SSLEngine on
# Server Certificate:
# Point SSLCertificateFile at a PEM encoded certificate. If
# the certificate is encrypted, then you will be prompted for a
# pass phrase. Note that a kill -HUP will prompt again. Keep
# in mind that if you have both an RSA and a DSA certificate you
# can configure both in parallel (to also allow the use of DSA
# ciphers, etc.)
# Some ECC cipher suites (http://www.ietf.org/rfc/rfc4492.txt)
# require an ECC certificate which can also be configured in
# parallel.
SSLCertificateFile "${SRVROOT}/conf/EntrustCert.pem"
#SSLCertificateFile "${SRVROOT}/conf/server-dsa.crt"
#SSLCertificateFile "${SRVROOT}/conf/server-ecc.crt"
# Server Private Key:
# If the key is not combined with the certificate, use this
# directive to point at the key file. Keep in mind that if
# you've both a RSA and a DSA private key you can configure
# both in parallel (to also allow the use of DSA ciphers, etc.)
# ECC keys, when in use, can also be configured in parallel
SSLCertificateKeyFile "${SRVROOT}/conf/private.pem"
#SSLCertificateKeyFile "${SRVROOT}/conf/server-dsa.key"
#SSLCertificateKeyFile "${SRVROOT}/conf/server-ecc.key"
Restart Apache
After making these changes you should be able to restart Apache and navigate to https://localhost without a security warning and a little padlock!
I hope this helps someone!
Sources:
1.) Auri Rahimzadeh's answer on creating a self-signed certificate
2.) Entrust Datacard - How do I convert a .pfx to be used with an Apache server?
- 872
- 1
- 13
- 21
-
1Thank you--worked for me using Windows 10, Apache24. Firefox warned that my certificate was self-signed but after I proceeded anyway, the lock icon is marked with a warning flag stating that I have granted an exception to it. – Dale Thompson Jul 26 '20 at 20:34
2021 Update
I’m posting this answer since I struggled with this myself and Chrome updated their security with requiring Subject Alternative Name which a lot of posts do not have as it was not required when they were posted as an answer. I’m assuming that WAMP is already installed.
STEP 1
Download OpenSSL Light and install
**STEP 2 (Optional)**
Although this part is optional, but it makes it easier later to execute commands. If you skip this step, you’ll have to provide full path to openssl.exe where you will execute the command. If you prefer to set it then update the openssl.exe path in Environment Variables.
Environment Variables -> System Variables -> Path -> Edit -> New -> c:\Program Files\OpenSSL-Win64\bin
**STEP 3**
Create a folder named “key” in the c:/wamp64/bin/apache/apache2.4.27(your version number)/conf/ directory.
Create configuration file for your CA MyCompanyCA.cnf with contents (you can change it to your needs):
[ req ]
distinguished_name = req_distinguished_name
x509_extensions = root_ca
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_min = 2
countryName_max = 2
stateOrProvinceName = State or Province Name (full name)
localityName = Locality Name (eg, city)
0.organizationName = Organization Name (eg, company)
organizationalUnitName = Organizational Unit Name (eg, section)
commonName = Common Name (eg, fully qualified host name)
commonName_max = 64
emailAddress = Email Address
emailAddress_max = 64
[ root_ca ]
basicConstraints = critical, CA:true
Create the extensions configuration file MyCompanyLocalhost.ext for your web server certificate:
subjectAltName = @alt_names
extendedKeyUsage = serverAuth
[alt_names]
DNS.1 = localhost
DNS.2 = mycy.mycompany.com
**STEP 4**
Execute these commands in the given order to generate the key and certificates:
openssl req -x509 -newkey rsa:2048 -out MyCompanyCA.cer -outform PEM -keyout MyCompanyCA.pvk -days 10000 -verbose -config MyCompanyCA.cnf -nodes -sha256 -subj "/CN=MyCompany CA"
openssl req -newkey rsa:2048 -keyout MyCompanyLocalhost.pvk -out MyCompanyLocalhost.req -subj /CN=localhost -sha256 -nodes
openssl x509 -req -CA MyCompanyCA.cer -CAkey MyCompanyCA.pvk -in MyCompanyLocalhost.req -out MyCompanyLocalhost.cer -days 10000 -extfile MyCompanyLocalhost.ext -sha256 -set_serial 0x1111
As a result, you will have MyCompanyCA.cer, MyCompanyLocalhost.cer and MyCompanyLocalhost.pvk files.
**STEP 5**
Install MyCompanyCA.cer under
Control Panel -> Manage User Certificates -> Trusted Root Certification Authorities -> Certificates
To install MyCompanyLocalhost.cer just double click it.
**STEP 6**
Open c:/wamp64/bin/apache/apache2.4.27(your version number)/conf/httpd.conf and un-comment (remove the #) the following 3 lines:
LoadModule ssl_module modules/mod_ssl.so
Include conf/extra/httpd-ssl.conf
LoadModule socache_shmcb_module modules/mod_socache_shmcb.so
**STEP 7**
Open c:/wamp64/bin/apache/apache2.4.37/conf/extra/httpd-ssl.conf and change all the parameters to the ones shown below:
Directory "c:/wamp64/www"
DocumentRoot "c:/wamp64/www"
ServerName localhost:443
ServerAdmin admin@example.com
ErrorLog "c:/wamp64/bin/apache/apache2.4.27/logs/error.log"
TransferLog "c:/wamp64/bin/apache/apache2.4.27/logs/access.log"
SSLCertificateFile "c:/wamp64/bin/apache/apache2.4.27/conf/key/MyCompanyLocalhost.cer"
SSLCertificateKeyFile "c:/wamp64/bin/apache/apache2.4.27/conf/key/MyCompanyLocalhost.pvk"
SSLSessionCache "shmcb:c:/wamp64/bin/apache/apache2.4.27/logs/ssl_scache(512000)"
CustomLog "c:/wamp64/bin/apache/apache2.4.27/logs/ssl_request.log" \
"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
Note: This is the tricky part. If you make any small mistake while editing this file, SSL won’t work. Make a copy of it before you edit it.
**STEP 8**
Restart Wamp and Chrome. Localhost is now secure: https://localhost
- 5,026
- 6
- 30
- 46
-
-
-
Could you possibly present a sample script? It'd be great to be able to do an automated install of this using Powershell or BAT. Thanks. – Ifedi Okonkwo Dec 06 '20 at 10:25
-
`unable to find 'distinguished_name' in config problems making Certificate Request 18140:error:0E06D06C:configuration file routines:NCONF_get_string:no value:crypto\conf\conf_lib.c:273:group=req name=distinguished_name` – Scott Fleming Feb 16 '21 at 15:31
This should be work Ubuntu, Mint similar with Apache2
It is a nice guide, so following this
and leaving your ssl.conf like this or similar similar
<VirtualHost _default_:443>
ServerAdmin your@email.com
ServerName localhost
ServerAlias www.localhost.com
DocumentRoot /var/www
SSLEngine on
SSLCertificateFile /etc/apache2/ssl/apache.crt
SSLCertificateKeyFile /etc/apache2/ssl/apache.key
you can get it.
Hope this help for linuxer
- 5,681
- 5
- 40
- 48
It's very simple,
just run the following commands
sudo a2enmod ssl
sudo service apache2 restart
sudo a2ensite default-ssl.conf
That's it, you are done.
If you want to force SSL (to use https always), edit the file:
sudo nano /etc/apache2/sites-available/000-default.conf
and add this one line
<VirtualHost *:80>
. . .
Redirect "/" "https://your_domain_or_IP/"
. . .
</VirtualHost>
then restart again
sudo service apache2 restart
- 1,920
- 19
- 19
-
And you need to run `systemctl reload apache2` after `sudo a2ensite default-ssl.conf`. – untill Mar 14 '19 at 10:23
This HowTo for CentOS was easy to follow and only took about 5 minutes: https://wiki.centos.org/HowTos/Https
I won't detail each step here, but the main steps are:
1.) Install the openssl module for apache, if not already installed
2.) Generate a self-signed certificate
--At this point, you should be able to visit https://localhost successfully
3.) Set up a virtual host if needed
- 3,243
- 3
- 23
- 37
This worked on Windows 10 with Apache24:
1 - Add this at the bottom of C:/Apache24/conf/httpd.conf
Listen 443
<VirtualHost *:443>
DocumentRoot "C:/Apache24/htdocs"
ServerName localhost
SSLEngine on
SSLCertificateFile "C:/Apache24/conf/ssl/server.crt"
SSLCertificateKeyFile "C:/Apache24/conf/ssl/server.key"
</VirtualHost>
2 - Add the server.crt and server.key files in the C:/Apache24/conf/ssl folder. See other answers on this page to find those 2 files.
That's it!
- 399
- 1
- 2
- 11
-
Yes this works. I used step 1 - 3 from StephanieQ to generate the certificate and than "openssl x509 -req -in server.csr -signkey server.key -out server.crt" to generate the *.crt file with cygwin. – aLx13 Apr 08 '19 at 14:31
-
I don't have an `httpd.conf`, what file do I put it in? Here's what happens when I put this text inside `apache2.conf`:`Invalid command 'SSLEngine', perhaps misspelled or defined by a module not included in the server configuration` – Aaron Franke Jul 13 '20 at 01:01
tl;dr
ssh -R youruniquesubdomain:80:localhost:3000 serveo.net
And your local environment can be accessed from https://youruniquesubdomain.serveo.net
Serveo is the best
- No signup.
- No install.
- Has HTTPS.
- Accessible world-wide.
- You can specify a custom fix, subdomain.
- You can self host it, so you can use your own domain, and be future proof, even if the service goes down.
I couldn't believe when I found this service. It offers everything and it is the easiest to use. If there would be such an easy and painless tool for every problem...
- 29,531
- 22
- 131
- 165
-
This doesn't work anymore in 2020, the page loads forever. However, for some reason the SSH command still works...? – Aaron Franke Jul 13 '20 at 00:53
I'd like to add something to the very good answer of @CodeWarrior, that works perfectly on Chrome, but for Firefox needs an additional step.
Since Firefox does not thrust CA Certificates that Windows does by default, you need to go on about:config, scroll down to security.enterprise_roots.enabled and change it to true.
Now your certificate should be seen as valid also on Firefox.
Of course this is only for development purposes, since ssl trust is a critical security concern and change this settings only if you know the implications.
- 1,221
- 1
- 12
- 17
Another simple method is using Python Server in Ubuntu.
Generate server.xml with the following command in terminal:
openssl req -new -x509 -keyout server.pem -out server.pem -days 365 -nodesNote: Assuming you have openssl installed.
Save below code in a file named
simple-https-server.pyin any directory you want to run the server.import BaseHTTPServer, SimpleHTTPServer import ssl httpd = BaseHTTPServer.HTTPServer(('localhost', 4443), SimpleHTTPServer.SimpleHTTPRequestHandler) httpd.socket = ssl.wrap_socket (httpd.socket, certfile='./server.pem', server_side=True) httpd.serve_forever()Run the server from terminal:
python simple-https-server.pyVisit the page at:
https://localhost:4443
Extra notes::
You can change the port in
simple-https-server.pyfile in linehttpd = BaseHTTPServer.HTTPServer(('localhost', 4443), SimpleHTTPServer.SimpleHTTPRequestHandler)You can change
localhostto your IP in the same line above:httpd = BaseHTTPServer.HTTPServer(('10.7.1.3', 4443), SimpleHTTPServer.SimpleHTTPRequestHandler)and access the page on any device your network connected. This is very handy in cases like "you have to test HTML5 GeoLocation API in a mobile, and Chrome restricts the API in secure connections only".
Gist: https://gist.github.com/dergachev/7028596
http://www.piware.de/2011/01/creating-an-https-server-in-python/
- 16,864
- 10
- 77
- 99
For those using macOS this is a great guide https://getgrav.org/blog/macos-sierra-apache-multiple-php-versions to set up your local web dev environment. In its 3rd part https://getgrav.org/blog/macos-sierra-apache-ssl Andy Miller explains how to set up apache with a self-signed certificate:
This is the key command:
openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout server.key -out server.crt
But there are a few steps you need to follow, so check that out and good luck! ;)
- 2,178
- 26
- 31