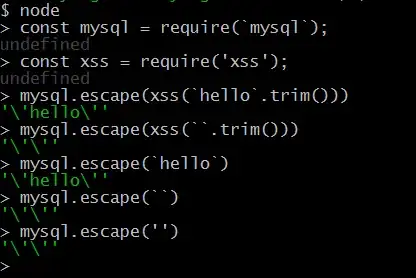
I will escape the parameter at first and then concat the sql string when querying.
So when I concat query strings using like:
const name = mysql.escape(req.info.name)
const sqlString = `select...name like '%${name}%'`
It will lead to select ... where name like '%'hello'%',
but what I want is select ... where name like '%hello%'