Once Managed Instance is deployed in the valid network/subnet, it will enforce some "Intent Policies" that prevent you from making some configurations that can invalidate the subnet.
As an example, Managed Instance can be deployed only in the subnet that don't contains other VMs. Once you deploy Managed Instance, it will setup intent rule that don't allow you to create VMs in this subnet and make the subnet invalid after deployment. Without these rules, you would be able to block access to Managed Instance. It cannot block everything, but this Intent Policy is the first-line of defense that Managed Instance uses to prevent someone to reconfigure the subnet.
Below is an example of the outbound rules that could be used in NSG.
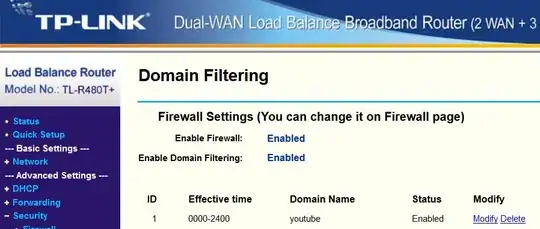
- Rule allow_management_inbound allows management traffic to reach the
instance.
- Rule allow_misubnet_inbound allows communication between
the virtual machines that form Managed Instance cluster.
- Rule allow_health_probe allows health check from the virtual machines
host. Without it service fabric will think that nodes are unhealthy
and block the access.
- Rule allow_tds_inbound is optional but without it yon can’t access the Managed Instance. It is advised to narrow its IP range as much as possible.
Priority numbers need not to be as depicted, but top 3 rules have to be of higher priority than any Deny rules.
To be compliant with Managed Instance Network Intent Policy, NSG must have rules that are numbered on picture as 100 and 200 on the top of the list.
- Rule allow_management_outbound allows management traffic to reach the services managed instance depends upon.
- Rule allow_misubnet_outbound allows communication between the virtual machines that form Managed Instance cluster.
Priority numbers need not to be as depicted, but top 2 rules have to be of higher priority than any Deny rules.
Managed Instance additional features may require additional ports to be open. This would be defined in the specific feature documentation.

