I sometimes get TLSv1 even when I set the version explicit to TLSv1.2.
I get this exception:
First chance exception at $75D917D2. Exception class EIdOSSLConnectError with message 'Error connecting with SSL. EOF was observed that violates the protocol'.
My Delphi version: Embarcadero® RAD Studio 10 Seattle Version 23.0.21418.4207
I am on Windows 10: Microsoft Windows [Version 10.0.17134.345]
My Indy Version: 10.6.2.5311 - That's what's coming with Seattle
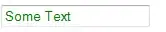
This is a trace when it works:
This is a trace when it does NOT work:
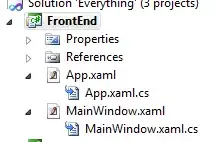
As you can see it is TLSv1. Why?
I had a look at following questions: Using Indy 10 IdHTTP with TLS 1.2 EIdOSSLConnectError Error connecting with SSL - EOF was observed
Here is my example code:
procedure TOpenWeatherFr.SetIcon(const IconCode: String);
var
HTTPS: TSSLHTTP;
MS : TMemoryStream;
PNG: TPngImage;
URL: string;
begin
HTTPS := TSSLHTTP.Create(nil);
MS := TMemoryStream.Create;
PNG := TPngImage.Create;
URL := 'https://openweathermap.org/img/w/' + IconCode + '.png';
try
(HTTPS.IOHandler as TIdSSLIOHandlerSocketOpenSSL).SSLOptions.SSLVersions := [sslvTLSv1_2];
HTTPS.Get(URL, MS);
MS.Seek(0, soFromBeginning);
PNG.LoadFromStream(MS);
Image1.Picture.Assign(PNG);
finally
HTTPS.Free;
PNG.Free;
MS.Free;
end;
Image1.Visible := true;
end;
For the sake of completeness here is the code of TSSLHTTP. The purpose is an old Indy version without SNI Support.
unit SSLHTTP;
interface
uses
Classes, IdHTTP, IdSSLOpenSSLHeaders, IdCTypes;
type
TSSLHTTP = class(TIdHTTP)
private
procedure OnStatusInfoEx(ASender: TObject; const AsslSocket: PSSL; const AWhere, Aret: TIdC_INT; const AType, AMsg: String);
public
constructor Create(AOwner: TComponent);
end;
implementation
uses
IdSSLOpenSSL;
{ TSSLHTTP }
constructor TSSLHTTP.Create(AOwner: TComponent);
begin
inherited Create(AOwner);
IOHandler := TIdSSLIOHandlerSocketOpenSSL.Create(self);
(IOHandler as TIdSSLIOHandlerSocketOpenSSL).OnStatusInfoEx := OnStatusInfoEx;
end;
procedure TSSLHTTP.OnStatusInfoEx(ASender: TObject; const AsslSocket: PSSL;
const AWhere, Aret: TIdC_INT; const AType, AMsg: String);
begin
SSL_set_tlsext_host_name(AsslSocket, Request.Host);
end;
end.
Where is my mistake? What am I doing wrong? This is the URL of the image I download: https://openweathermap.org/img/w/04d.png
EDIT: Adding paylod as hex dumb
Working payload - Client Hello:
0000 16 03 01 01 49 01 00 01 45 03 03 8b 3d e5 54 59
0010 f8 59 44 82 f7 14 92 45 50 e1 a3 86 68 3a c2 94
0020 76 be ea 8b 54 98 f3 27 69 50 af 00 00 94 c0 30
0030 c0 2c c0 28 c0 24 c0 14 c0 0a 00 a3 00 9f 00 6b
0040 00 6a 00 39 00 38 c0 32 c0 2e c0 2a c0 26 c0 0f
0050 c0 05 00 9d 00 3d 00 35 00 88 00 87 00 84 c0 2f
0060 c0 2b c0 27 c0 23 c0 13 c0 09 00 a2 00 9e 00 67
0070 00 40 00 33 00 32 c0 31 c0 2d c0 29 c0 25 c0 0e
0080 c0 04 00 9c 00 3c 00 2f 00 9a 00 99 00 45 00 44
0090 00 96 00 41 00 07 c0 11 c0 07 c0 0c c0 02 00 05
00a0 00 04 c0 12 c0 08 00 16 00 13 c0 0d c0 03 00 0a
00b0 00 15 00 12 00 09 00 14 00 11 00 08 00 06 00 03
00c0 00 ff 01 00 00 88 00 00 00 17 00 15 00 00 12 6f
00d0 70 65 6e 77 65 61 74 68 65 72 6d 61 70 2e 6f 72
00e0 67 00 0b 00 04 03 00 01 02 00 0a 00 34 00 32 00
00f0 0e 00 0d 00 19 00 0b 00 0c 00 18 00 09 00 0a 00
0100 16 00 17 00 08 00 06 00 07 00 14 00 15 00 04 00
0110 05 00 12 00 13 00 01 00 02 00 03 00 0f 00 10 00
0120 11 00 23 00 00 00 0d 00 20 00 1e 06 01 06 02 06
0130 03 05 01 05 02 05 03 04 01 04 02 04 03 03 01 03
0140 02 03 03 02 01 02 02 02 03 00 0f 00 01 01
Not working payload - Client hello:
0000 16 03 01 01 49 01 00 01 45 03 03 f6 7b de 81 5d
0010 76 74 a7 31 99 36 8d 17 4c 07 5e 73 5d f7 b8 a1
0020 4f 06 5e 91 e5 f0 4b 37 0d 65 e7 00 00 94 c0 30
0030 c0 2c c0 28 c0 24 c0 14 c0 0a 00 a3 00 9f 00 6b
0040 00 6a 00 39 00 38 c0 32 c0 2e c0 2a c0 26 c0 0f
0050 c0 05 00 9d 00 3d 00 35 00 88 00 87 00 84 c0 2f
0060 c0 2b c0 27 c0 23 c0 13 c0 09 00 a2 00 9e 00 67
0070 00 40 00 33 00 32 c0 31 c0 2d c0 29 c0 25 c0 0e
0080 c0 04 00 9c 00 3c 00 2f 00 9a 00 99 00 45 00 44
0090 00 96 00 41 00 07 c0 11 c0 07 c0 0c c0 02 00 05
00a0 00 04 c0 12 c0 08 00 16 00 13 c0 0d c0 03 00 0a
00b0 00 15 00 12 00 09 00 14 00 11 00 08 00 06 00 03
00c0 00 ff 01 00 00 88 00 00 00 17 00 15 00 00 12 6f
00d0 70 65 6e 77 65 61 74 68 65 72 6d 61 70 2e 6f 72
00e0 67 00 0b 00 04 03 00 01 02 00 0a 00 34 00 32 00
00f0 0e 00 0d 00 19 00 0b 00 0c 00 18 00 09 00 0a 00
0100 16 00 17 00 08 00 06 00 07 00 14 00 15 00 04 00
0110 05 00 12 00 13 00 01 00 02 00 03 00 0f 00 10 00
0120 11 00 23 00 00 00 0d 00 20 00 1e 06 01 06 02 06
0130 03 05 01 05 02 05 03 04 01 04 02 04 03 03 01 03
0140 02 03 03 02 01 02 02 02 03 00 0f 00 01 01