I've created a VPC with IPv4 CIDR 172.16.0.0/16, next I've created three subnets:
- subnet_1 172.16.0.0/20
- subnet_2 172.16.16.0/20
- subnet_3 172.16.32.0/20
Next I created an Internet Gateway attached to the VPC.
At this point I've created an EC2 instance and I attached to it an Elastic IP. On this instance I have installed an OpenVPN access server.
I then created a second EC2 instance that only has a private IP address. In my mind I thought that once connected via VPN I should able to ssh into the second EC2 instance with a private IP, but I'm not able to connect. What might I have done wrong?
EDIT: I edit the post with some additional information
This is how I configured my VPC

My subnets attached to the VPC
The internet gateway attached to VPC

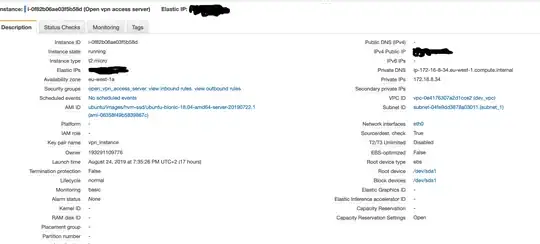
This is my EC2 instance with OpenVpn access server, with his Elastic Ip so that I can access from my browser
Inbound rules for security group of vpn instance
The second and private instance (the instance to which I want to connect via VPN)
In OpenVpn access server I do this configurations
And when I connect to the VPN I receive this address 172.16.128.2 (for example)