I'm having an issue with a Service Account which has Role attached to it called Preemptible Killer.
The role is bound to this service account, I even gave it "Editor" access for debugging purposes.
I have a single project and I double-checked that the names are correct.
I'm having an issue when I get a 403 when hitting the delete instance API. If I go to the Policy Troubleshooter I can see that in theory, it has the right amount of access.
Access granted for API call for preemptible-killer@{project}.iam.gserviceaccount.com, compute.instances.delete, instances/{instance}.
However, when it gets called from my K8s cluster node I get a 403. Here are the unexpected 403, service account and roles screenshots. I'm definitely missing something I just don't know what.
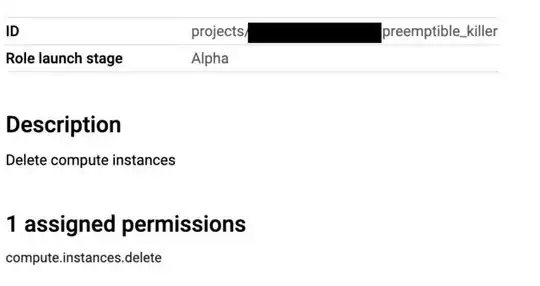
This is the role:
This is the custom role + editor roles attached to the Service Account.
❯ gcloud projects get-iam-policy {project}
bindings:
- members:
- serviceAccount:preemptible-killer@{project}.iam.gserviceaccount.com
role: projects/{project}/roles/preemptible_killer
- members:
- serviceAccount:preemptible-killer@{project}.iam.gserviceaccount.com
role: roles/editor