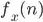I got this issue while trying to fetch user attributes from AWS Cognito.
I can't tell how it can be an "Invalid Token" because I have copied and pasted it, also I have make sure that it's the accessToken not idToken or anything else.
There are some other similar questions on this site but they don't address my issue:
"Access token does not contain openid scope" in AWS Cognito
Access token does not have the openid scope
Update: here my app client config