If you open the network panel on any webpage that contains scripts, images, stylesheets or fonts you will see that all those requests are done using GET HTTP method. For example this is how a request for a file loaded by a <script> tag looks like:
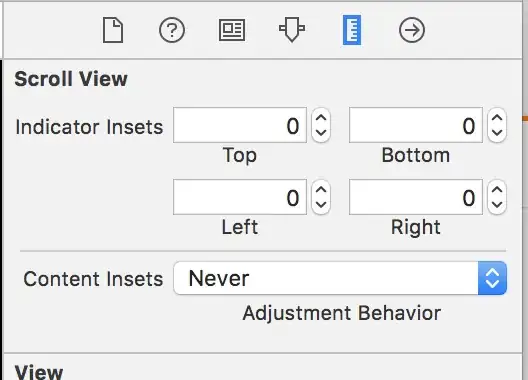
And this is an example for an file loaded by an <img> tag looks like:
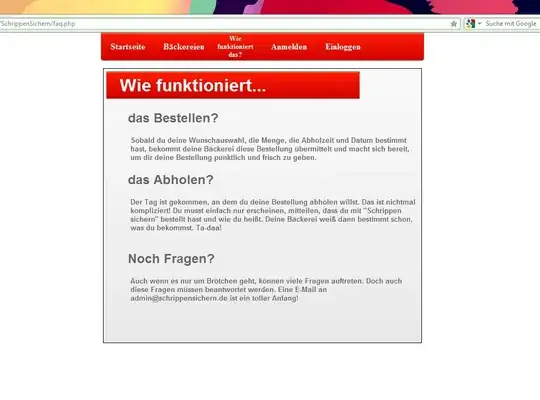
Browser will just blindly trust you that if you are loading such a resource from anywhere you know what you are doing and it will fetch it for you (otherwise things like CDN would not work) as opposed to an XHR request!
XHR requests (including fetch calls) are checked against CORS policy, I believe you are familiar with what that is. JavaScript will not be able to make any XHR request for a resource that lives on a different domain (or port etc.).
So you have two types of request policies:
- Anything you fetch using XHR will be checked against CORS but you can pick whatever HTTP request method you want
- Anything you load using
img, script, link etc will not be checked against CORS policy but you are restricted to GET HTTP requests only. The browser will also send all the cookies along, most importantly the authentication ones in this case.
That means that if you are serving a JSON array using GET you can use a script tag to fetch it for you no matter which domain you are on. Then, using the trick mentioned in the article, you can execute the array (sounds weird but yes) and grab the sensitive information.
If you'd be using POST, the attacker has no way of using a script (or any other) tag to perform this request since they use GET requests to fetch resources.
You could think Ah but I can use form to do that! but you will run into the same CORS issues. If you just submit a form, the JSON data will load into the current page and there is no way for you as an attacker to get it since your script no longer exists on the page.
You could think Ah I just set the form target to an iframe! but JavaScript will not allow you to access anything within that iframe.
Does that make sense?

