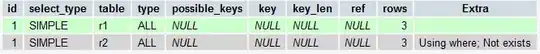
I got the same problem. Also used the example code from here
The only adjustment to the example code is creating the session. here there was always an error message with the example code.
My code:
index.js:
// index.js
var express = require('express');
var app = express();
const cors = require('cors');
app.use(cors());
const session = require('express-session');
const memoryStore = new session.MemoryStore();
app.use(session({
secret: 'some secret',
resave: false,
saveUninitialized: true,
store: memoryStore
}));
const keycloak = require('./config/keycloak-config.js').initKeycloak(memoryStore);
app.use(keycloak.middleware({
logout: '/logout',
admin: '/'
}));
const testController = require('./controller/test-controller.js');
app.use('/test', testController);
app.get('/', function (req, res) {
res.send("Server is up!");
});
app.listen(3000);
keycloak-config.js:
// keycloak-config.js
var session = require('express-session');
var Keycloak = require('keycloak-connect');
let _keycloak;
var keycloakConfig = {
clientId: 'test-client',
bearerOnly: true,
serverUrl: 'http://localhost:8080/auth',
realm: 'test',
credentials: {
secret: 'xS9K7RpUah5PzWQZh6BaAGX8Ochr6RY6'
}
};
function initKeycloak(memoryStore) {
if (_keycloak) {
console.warn("Trying to init Keycloak again!");
return _keycloak;
}
else {
console.log("Initializing Keycloak...");
_keycloak = new Keycloak({
store: memoryStore
}
, keycloakConfig
);
return _keycloak;
}
}
function getKeycloak() {
if (!_keycloak){
console.error('Keycloak has not been initialized. Please called init first.');
}
return _keycloak;
}
module.exports = {
initKeycloak,
getKeycloak
};
test-controller.js:
// test-controller.js
var express = require('express');
var router = express.Router();
const keycloak = require('../config/keycloak-config.js').getKeycloak();
router.get('/anonymous', function(req, res){
res.send("Hello Anonymous");
});
router.get('/user', keycloak.protect('user'), function(req, res){
res.send("Hello User");
});
router.get('/admin', keycloak.protect('admin'), function(req, res){
res.send("Hello Admin");
});
router.get('/all-user', keycloak.protect(['user','admin']), function(req, res){
res.send("Hello All User");
});
module.exports = router;