I have a private certificate that was generated by azure for a web app for linux containers. I want to pass this value to my .net core app via the web app configuration settings in the the azure portal. This is part of a pipeline CI-CD process and the ability to specify Identity Server key values in app configuration helps to keep those values out of the source code.
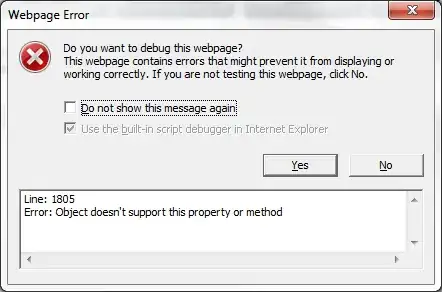
PROBLEM
I keep getting the following error by the setting
❌Key vault Reference
I am trying to use the secret value in the format suggested by the microsoft docs here I have tried the following formats:
@Microsoft.KeyVault(https://myvault.vault.azure.net/secrets/myCertName/versionGUID)
@Microsoft.KeyVault(VaultName=myvault;SecretName=myCertName;SecretVersion=versionGUID)
ALSO, I have added the web app to the access policies of the azure key vault
EDIT 1:
There was a format error and I had the wrong secret name so the following format worked:
@Microsoft.KeyVault(https://myvault.vault.azure.net/secrets/myCertName/versionGUID)
However I ran into a new error:
Key Vault reference was not able to be resolved because site Managed Identity not enabled MSINotEnabled
SO I went to the identity tab of the web app and turned on managed identity for the app.
I am now stuck with the following error:
Key Vault reference was not able to be resolved because site was denied access to Key Vault reference's vault.
I found multiple sites that said if you just deleted the setting, saved, and then add the setting back it should resolve. This DID NOT work for me.
I also tried granting "Full access" to the web app in the azure key vault access policies.