I'm trying to capture the unencrypted bytes of a TLS connection and record them into a cap file for analysis of the HTTP/2 traffic. There are a lot of assumptions I am making that this is even possible. But I'm willing to fudge almost everything below the HTTP/2 layer if I can see that traffic in a useful tool like Wireshark.
My approach eventually boils down to
return object : DelegatingSSLSocket(socket) {
override fun getInputStream(): InputStream {
return object : FilterInputStream(socket.inputStream) {
override fun read(b: ByteArray, off: Int, len: Int): Int {
return super.read(b, off, len).also { readLen ->
dumper.dump(
ipv4ReadPacketBuilder.payloadBuilder(
tcpReadPacketBuilder
.payloadBuilder(
UnknownPacket.Builder().rawData(
b.sliceArray(off.rangeTo(off + readLen))
)
)
)
.build()
)
}
}
}
}
override fun getOutputStream(): OutputStream {
return object : FilterOutputStream(socket.outputStream) {
override fun write(b: ByteArray, off: Int, len: Int) {
super.write(b, off, len)
dumper.dump(
ipv4WritePacketBuilder.payloadBuilder(
tcpWritePacketBuilder
.payloadBuilder(
UnknownPacket.Builder().rawData(b.sliceArray(off.rangeTo(off + len)))
)
)
.build()
)
}
}
}
}
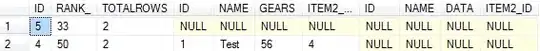
Does anyone have any advice on pcap4j or pcap files generally to see what I'm doing wrong?
The packets I'm writing are IPv4>TCP>Data
But Wireshark shows