I am using runbook in Azure Automation Account. In this runbook, i use "run as account" which has Owner rights on the subscription. When i execute the command Get-AzRoleAssignment, i get:
Get-AzRoleAssignment : Exception of type 'Microsoft.Rest.Azure.CloudException' was thrown.
At line:21 char:16 + $listOfUsers = Get-AzRoleAssignment -verbose + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ +
CategoryInfo : CloseError: (:) [Get-AzRoleAssignment], CloudException + FullyQualifiedErrorId :
Microsoft.Azure.Commands.Resources.GetAzureRoleAssignmentCommand
the Service Principal of "run as account" has below permissions:
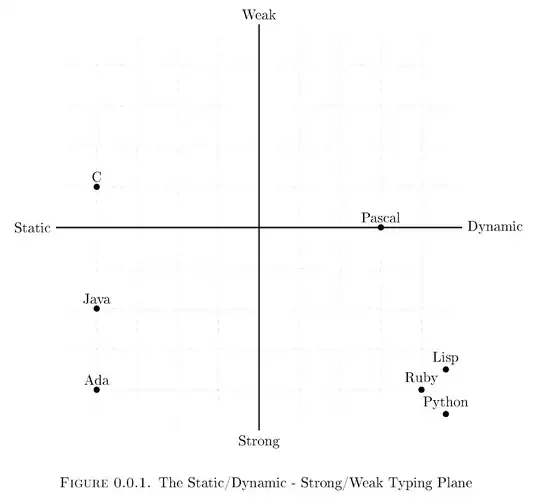
Do you have any idea?
Is it an authorization error? If so, which permissions should i give to the SP?