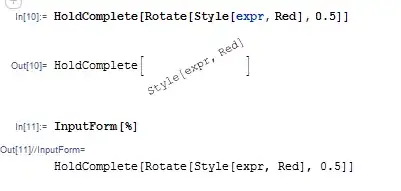
I have the below structure for my spring boot 2.5.5 application where the client request reaches Server A which is then forwarded to Server B and then Server C.
I have implemented Spring Security and AD SAML Authentication using (spring-security-saml2-core)
- Nginx (Server A) -> nginx.conf as been configured for proxy pass to Server B
- Nginx (Server B) -> nginx.conf as been configured for proxy pass to Server C
- Tomcat (Server C) -> Actual Spring Boot App deployed here
Now in Azure AD we create the App and get the Entity Id, Metadata URL and Reply URL [https://serverA/appName] the same are configured in my Spring Boot Application.
After all this configuration when we access the app from the client I am able to get the SSO Login page and I can enter the credentials. Once I try to log in I get the below exception listed on the Server C logs
SAML message intended destination endpoint 'https://serverA/appName/saml/SSO' did not match the recipient endpoint 'https://serverB/appName/saml/SSO'