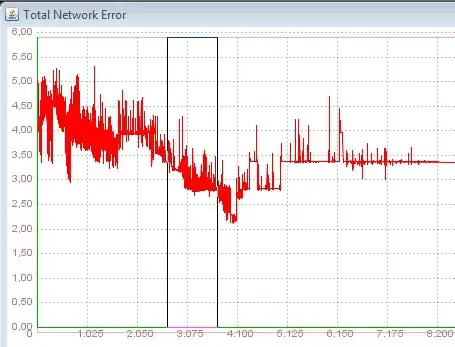
System.Net.WebException:
java.security.cert.CertPathValidatorException: Trust anchor for certification path not found.'
This is an error that occurs in my VS2022 solution when working with a self signed certificate and Android.
The case is the following:
It is an android app that runs on an local network, with a local https backend service. A certificate has been issued for this service by the domain admin. However, the domain is not an official CA (Certificate Authority). You then have to manually install a CA, via settings.
Part of the solution
What I did to solve this is adding the CA certificates to the Android device (via Settings > Security -> Encryption & Credentials -> Install a Certificate).
The web browser, in the android app, can now successfully access the https site, without warnings.
I still need help with
However the CA store is not accessible via the app unless it is configured via network-security-config: https://developer.android.com/training/articles/security-config#TrustingAdditionalCas
This is something that can be done in the Xamarin days like:
- https://devblogs.microsoft.com/xamarin/cleartext-http-android-network-security/
- https://nicksnettravels.builttoroam.com/android-certificates/#:~:text=Accessing%20the%20Android%20Certificate%20Store
But in MAUI I'm a bit lost, I don't see the right resources, mipmap, etc.
I would like to solve this issue with a one-liner like this:
[assembly: Application(UsesCleartextTraffic = true)]
...which can also be configured via the via network-security-config.
Is there a one-liner or can someone help me out configuring my network-security-config to get the CA store available in a MAUI solution?