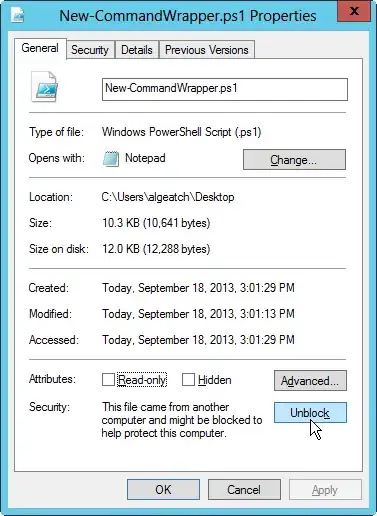
I am trying to execute a script from shared folder that I trust:
PowerShell -file "\\server\scripts\my.ps1"
But I get a security warning, and have to press 'R' to continue
Security Warning Run only scripts that you trust. While scripts from the Internet can be useful, this script can potentially harm your computer. Do you want to run \server\scripts\my.ps1? [D] Do not run [R] Run once [S] Suspend [?] Help (default is "D"): d
Can I ignore this warning? The desired pseudo code I want is:
PowerShell -IGNORE_SECURITY_WARNING -file "\\server\scripts\my.ps1"