What is the action of the "Grpl" instruction in the I386 instruction set? I am learning about computer instruction and doing instruction simulation experiments. During the simulation I encountered such an instruction 83 F8 01.
To find out what to do with this instruction, I consulted Appendix a Opcode Map in the i386 manual. Since the opcode by of the instruction is 83, I found the opcode map entry:
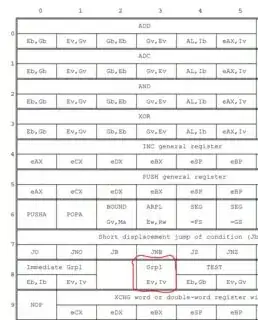
But I don't know what the GRPL means or what the CPU does. I checked the Intel 80386 Instruction Set and couldn't find a description of the Instruction. Instructions that begin with E are followed directly by instructions that begin with H. (enter and hlt)
I also looked up Google and couldn't find a description of the command. Not knowing the actual meaning of this instruction, I had no way to simulate it. How does the CPU implement this? What is the correct query? Do I miss something?