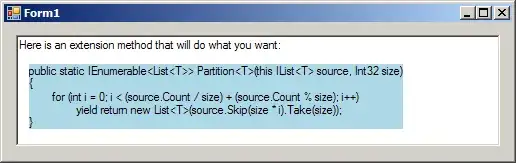
AWS Control Tower installs aws-controltower-GuardrailsComplianceAggregator as an AWS Config Aggregator in the Audit account, referencing all accounts (except Master) as source accounts. However, the config aggregator does not have access to the data in these accounts (except itself), and the status is listed as "Failed" with the error message "AWS Config does not have permission from the source account to replicate data into an aggregator account. Authorize aggregator account to replicate data from source accounts and region."
It was my belief that Control Tower would configure the required roles and resources for this to work seamlessly. There are instructions on how to fix this in AWS Config (https://aws.amazon.com/premiumsupport/knowledge-center/config-aggregator-accounts/), but I thought Control Tower would do this for me. Also, those instruction seem to require manual setup in each source region, while the Control Tower aggregator automatically includes future AWS regions -- another hint that there is something missing here.
I guess the questions are these:
- Is this expected behavior in Control Tower?
- What do I need to do to fix this using Control Tower?
The screenshot below is from a brand new Control Tower setup, with a new master account, new audit and logarchive accounts, and one new normal account from the control tower account factory. The logarchive and normal accounts have status "Failed", while the audit account has status "OK". It's using Control Tower version 3.0.