On my website, all of a sudden I cannot upload photos. I get the following error:
##### RightAws::S3Interface returned an error: 400 Bad Request
<?xml version="1.0" encoding="UTF-8"?>
<Error><Code>InvalidBucketAclWithObjectOwnership</Code><Message>Bucket cannot have ACLs set with ObjectOwnership's BucketOwnerEnforced setting</Message><RequestId>REQUEST</RequestId><HostId>ID$
##### RightAws::S3Interface request: https://bucket.s3.amazonaws.com:443/ ####
RightAws::AwsError (InvalidBucketAclWithObjectOwnership: Bucket cannot have ACLs set with ObjectOwnership's BucketOwnerEnforced setting):
What's odd, is nothing has been changed on my end, when this used to work. AWS did send out this email, which seems related but was only supposed to apply to new buckets:
Hello,
We are reaching out to inform you that starting in April 2023 Amazon S3 will change the default security configuration for all new S3 buckets. For new buckets created after this date, S3 Block Public Access will be enabled, and S3 access control lists (ACLs) will be disabled.
The majority of S3 use cases do not need public access or ACLs. For most customers, no action is required. If you have use cases for public bucket access or the use of ACLs, you can disable Block Public Access or enable ACLs after you create an S3 bucket. In these cases, you may need to update automation scripts, CloudFormation templates, or other infrastructure configuration tools to configure these settings. To learn more, read the AWS News blog [1] and What's New announcement [2] on this change or visit our user guide for S3 Block Public Access [3] and S3 Object Ownership to disable ACLs [4]. Also, see our user guide for AWS CloudFormation on these settings [5][6].
I have seen similar issues, where people fixed it by using Edit Object Ownership to set Object Ownership to ACLs disabled (recommended). When I try this I get this error:
Bucket owner enforced cannot be applied because you have existing bucket ACLs If you want to apply the bucket owner enforced setting, you must remove access granted to other AWS accounts or groups from your bucket ACL and migrate these permissions to a bucket policy
I'm not sure how to get past this. I've seen people update the Bucket Policy, but mine is currently blank. I'm fairly new to AWS so I'm being careful not to mess with too much I don't understand.
This bucket should be public. This is the current ACL settings:
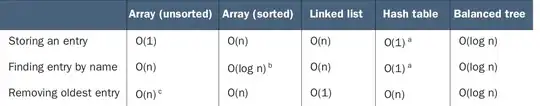
I attempted to move over to using a Bucket Policy. I set my bucket policy as follows:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1380877761162",
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::bucketname/*"
}
]
}
I removed the Bucket ACLs to put them back to the defaults.
And I edited Object Ownership:
And still I get the same error, which is particularly confusing because if I understand correctly, it now should not be using ACLs at all.