I am trying to create Azure databricks scope programatically as I found that once a scope has been created, databricks will not be able to see any secrets created in Key vault after the scope has been created.
According to the Ms documentation, this can be done programmatically, see here.
I am doing this from a powershell terminal.
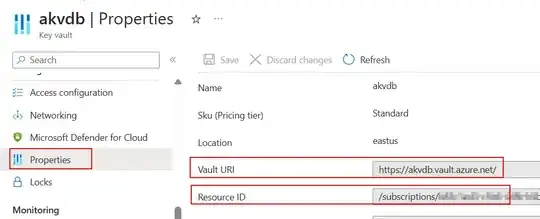
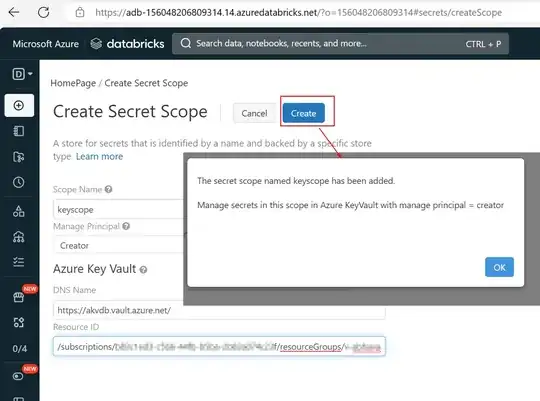
databricks secrets create-scope --scope my_scope --scope-backend-type AZURE_KEYVAULT --resource-id "/subscriptions/xxxx/resourceGroups/my-rg/providers/Microsoft.KeyVault/vaults/my-db-kv" --dns-name "https://my-db-kv.vault.azure.net/" --initial-manage-principal users
I then get the error.
Error: b'{"error_code":"INVALID_PARAMETER_VALUE","message":"Scope with Azure KeyVault must have userAADToken defined!"}'PS