i'm having problems understanding the verification and validation of a token.
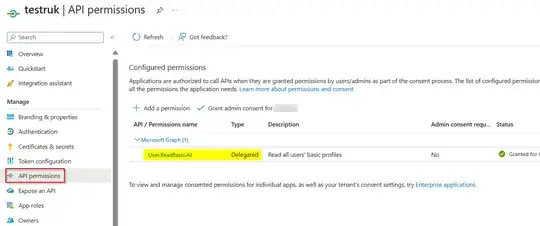
I have a server running that is registered on Azure with Application id = SERVER_ID
I also have a client application registered on azure with Application id = CLIENT_ID
In python with msal library, I can acquire a token for the server with the username and password workflow:
import msal
app = msal.PublicClientApplication(
client_id=SERVER_ID,
authority=f"https://login.microsoftonline.com/{TENANT_ID}",
)
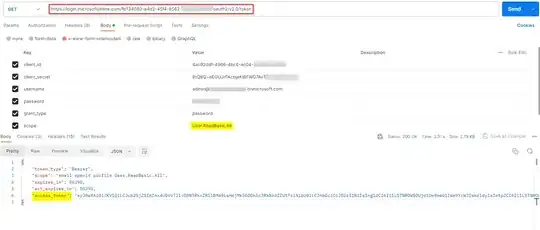
result = app.acquire_token_by_username_password(
USERNAME, PASSWORD, scopes=["User.ReadBasic.All"]
)
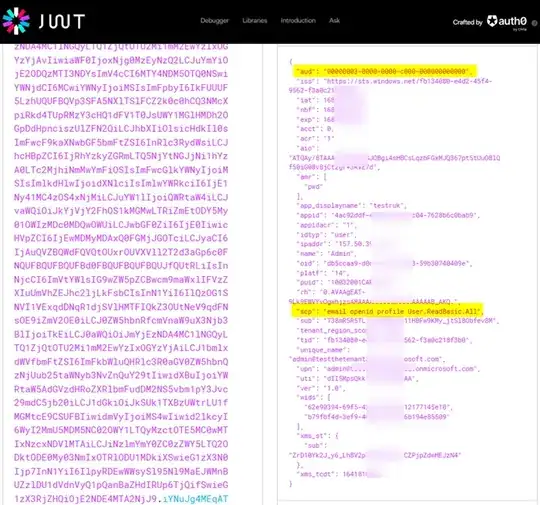
this result has inside an access_token and an id_token. I can successfully validate the id_token by using this library (https://github.com/yejianquan/gems/blob/823076051695029b4d699744dc76c959a8476230/src/python-azure-ad-token-validate/aadtoken/init.py)
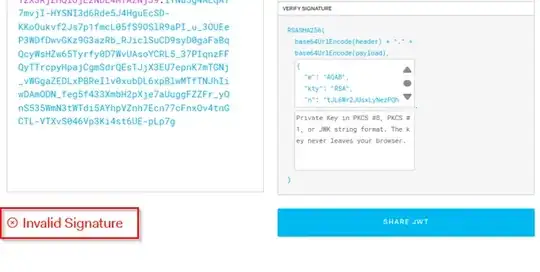
but cannot do the same with the access token.
On the other hand I can also get an access token for a client application like this:
import msal
app = msal.ConfidentialClientApplication(
client_id=CLIENT_ID,
client_credential="WAUISbaiud.askljdUHDIKAOUSDOAO",
authority=f"https://login.microsoftonline.com/{TENANT_ID}",
)
result = app.acquire_token_for_client(scopes=[f"{SERVER_ID}/.default"])
inside result there's only access_token that i can verify with the previous library.
Assuming i make requests to the server by adding the token in the headers:
headers = {
'Authorization': f'Bearer {token}',
'Content-Type': 'application/octet-stream',
}
response = response = requests.get(url, headers=headers)
which token should i use? the access_token or the id_token? if it's the access_token how should i validate it in case of the username/password workflow? do i have to use some private key? and when?
Many thanks