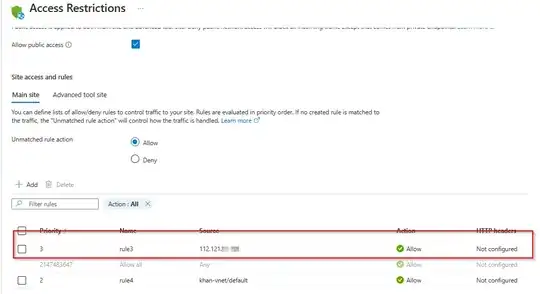
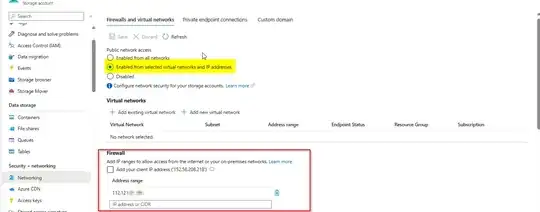
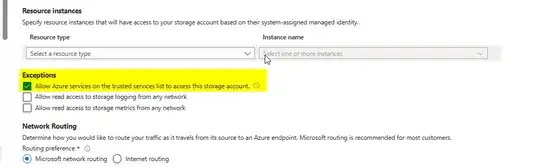
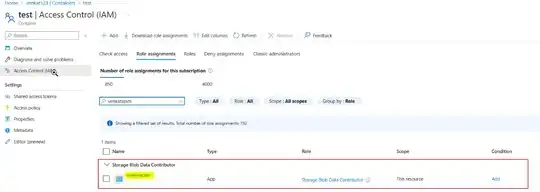
We have multiple backend APIs hosted on Azure web app under same plan. All APIs have same outbound ips, and all these APIs enabled access restriction, these APIs only accessible within the api gateway. We have blob storage, we have also enable restriction on it (Networking Enabled from selected virtual networks and IP addresses Firewall, added all APIs ips on it), Now when APIs going to fetch some image from blob it throw following error,
Azure.RequestFailedException: This request is not authorized to perform this operation.
RequestId:0bc5827d-c01e-0030-382f-929e61000000
Status: 403 (This request is not authorized to perform this operation.)
ErrorCode: AuthorizationFailure
Content:
<?xml version="1.0" encoding="utf-8"?><Error><Code>AuthorizationFailure</Code><Message>This request is not authorized to perform this operation.
RequestId:0bc5827d-c01e-0030-382f-929e61000000
Time:2023-05-29T13:11:56.0013545Z</Message></Error
Point to be noted that both APIs and blob are not using vNet, and both are on same resource group and using the same Identity but when we remove network restriction on storage account it works fine
](../../images/3820883082.webp)