Yes, a centralized log analytics workspace can be used as a Sentinel workspace to expedite log analysis and monitoring without having to connect to different resources separately.
To achieve this, create a Microsoft sentinel in the portal, link the workspaces that need to be linked while creating the sentinel, and enable UEBA. as detailed in MSDoc.
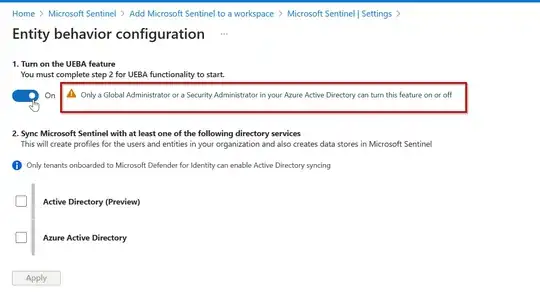
To enable this, go to Microsoft sentinel -> configuartion -> settings. you need to have either a global administrator or a security administrator privilege as shown.
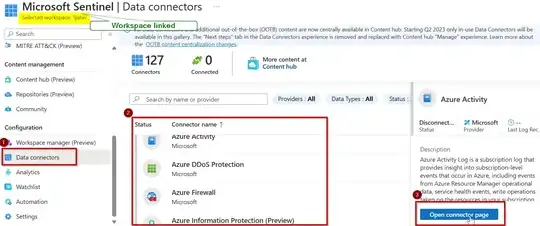
To connect the workspace logs to sentinel, scroll to Data connectors then search for Azure activity logs that need to be linked with sentinel. Then as shown, it redirects you to the connector page.
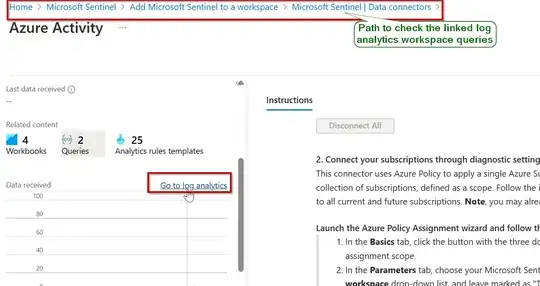
Once it is done, you can create workbooks and analytic rules which allows you to create a dashboard to visualize data and notify security alerts.
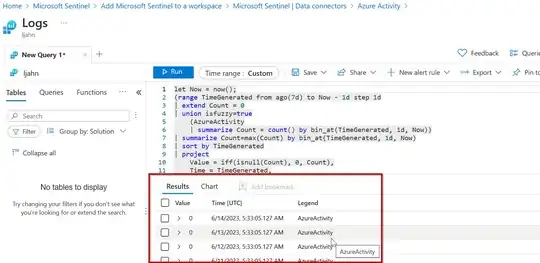
You can also query the individual workspace logs linked to the Sentinel as shown below.
Refer these Microsoft sentinel & Microsoft Q&A for more relevant approaches for this requirement.



