I have an application in Vue.js that obtains user/bearer tokens using oidc-client that gives information about the usergroups in a particular Enterprise Application in Azure AD, the current logged in user is part of. We have used the following as the scope scope: `openid email profile api://${APP_CLIENT_ID}/user_access' where APP_CLIENT_ID is the corresponding app registration application/client id. Now we are trying to implement the same from a desktop client app using MSAL but using the same scope with or without the "/.default" suffix provides errors. Also, have tried using "api://Resource URI/.default", which gives the token but does not provide any info on app Usergroups. What should be the correct scope that needs to be used to get the info or is there any other alternative to this?
Asked
Active
Viewed 116 times
1 Answers
0
To fetch the Azure AD group the current logged in user is part of, check the below:
Assign GroupMember.Read.All API permission to the Azure AD Application.
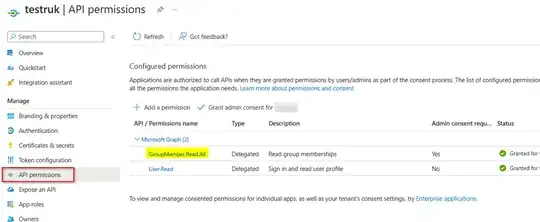
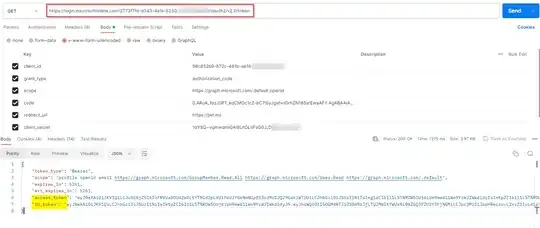
Now, generate access token to call Graph API via Postman like below:
https://login.microsoftonline.com/TenantID/oauth2/v2.0/token
client_id:ClientID
grant_type:authorization_code
scope:https://graph.microsoft.com/.default
code:code
redirect_uri:https://jwt.ms
client_secret:ClientSecret
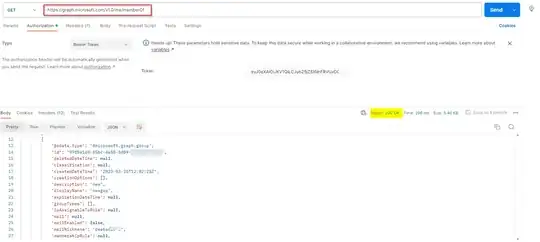
To get the Azure AD group the current logged in user is part of, use the below query:
https://graph.microsoft.com/v1.0/me/memberOf
To fetch the groups assigned to the Azure AD Application, check the below:
Add optional claim in the Azure AD Application:
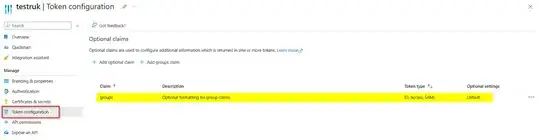
Now, I generated tokens via Postman using below parameters:
https://login.microsoftonline.com/TenantID/oauth2/v2.0/token
client_id:ClientID
grant_type:authorization_code
scope:https://graph.microsoft.com/.default
code:code
redirect_uri:https://jwt.ms
client_secret:ClientSecret
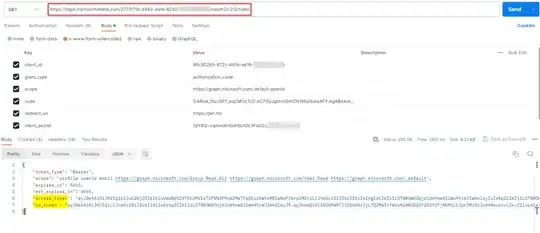
When I decoded the token, the groups added to the Application are displayed like below:

Rukmini
- 6,015
- 2
- 4
- 14
-
Yes. Using Postman, I am able to get correct bearer token. My question is how do I do it using MSAL or OIDC in C# programmatically – user9057272 Jun 27 '23 at 10:00
-
In MSAL set scope as `https://graph.microsoft.com/.default` and then generate the bearer token – Rukmini Jun 27 '23 at 10:01
-
Does these help https://github.com/AzureAD/microsoft-authentication-library-for-js/tree/dev/samples/msal-node-samples/auth-code and https://github.com/AzureAD/microsoft-authentication-library-for-dotnet/wiki/Acquiring-tokens-with-authorization-codes-on-web-apps? – Rukmini Jun 27 '23 at 10:54
-
Using the "https://graph.microsoft.com/.default" scope gives me a token but it does not provide the complete details like user email, id roles and groups – user9057272 Jun 27 '23 at 13:44
-
To get user email id you have to make seperate graph call using that token. – Rukmini Jun 27 '23 at 13:48
-
You can use `https://graph.microsoft.com/v1.0/me` and use $select to display your results. – Rukmini Jun 27 '23 at 13:48
-
Where do i need to use this? https://graph.microsoft.com/v1.0/me. If I use it in the scope for MSAL it gives me error. Again https://graph.microsoft.com/v1.0/me/.default also seems to give error – user9057272 Jun 30 '23 at 12:55
-
I am using GraphService client to fetch the App roles and groups but I need to provide and identifier like my email id or user object id. Is there any way of detecting my windows ID and mapping it to the Azure AD identity and connect to the Graph API? – user9057272 Jun 30 '23 at 12:57
-
1AFAIK there is no way. You have to pass object id or UPN to fetch groups and app roles. – Rukmini Jun 30 '23 at 15:06