I have a linux Web App on Azure (fastAPI) that currently has these responsibilites
- serves a Single Page Application (SPA)
- is a reverse proxy for the backend
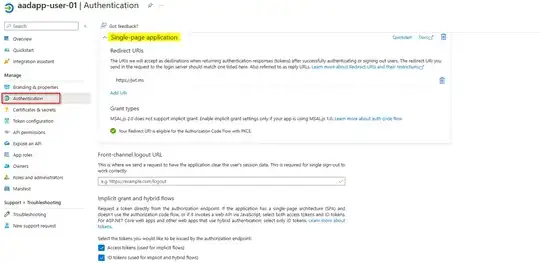
For this API, I use the built-in authentication feature "Easy Auth".
What I currently do is the following flow:
- User requests SPA -> is redirected to the identity provider -> authenticates himself, gets the a cookie injected into his browser and is redirected to the web app through the callback URL setup in the AAD App & gets the SPA code
- SPA then makes requests against the protected API with the injected cookie (HTTP cookie)
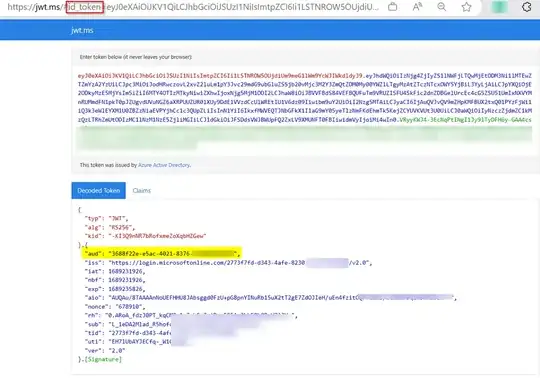
Because the SPA does not call the API with a auth token (bearer token), I want to exchange the cookie for an auth token on the server (API). For this, the API uses that cookie from the request to call the /.auth/me endpoint (blob storage token store) to get more information about the user, from which it can extract the id_token or the access_token.
From here, I noticed that the id_token can be used to call to another API that is protected by the same Azure AD App through EasyAuth.
However, the id_token is sometimes expired and calling the /.auth/refresh does only refresh the access_token.
Question(s):
General question: Why can the id_token be used to access the downstream API. I thought this is the job of the access_token?.
Edit: Turns out that:
The OAuth 2.0 implicit flow in Azure AD is designed to return an ID token when the resource for which the token is being requested is the same as the client application.
Actual question: Is there a way to also refresh the id_token without needing the user to re-authenticate? Similar to calling the /.auth/refresh endpoint? Or what would be the right approach? Or am I doing things completely wrong and the SPA should just get a auth token and then make requests against the API?
Simliar questions: