I have an Azure Function app in Python 3.9 that connects to an API and inserts data into a microsoft sql database. When running the code locally it works as expected. However when the app is running/hosted in Azure it gets an error:
sqlalchemy.exc.DBAPIError: (pyodbc.Error) ('HY000', '[HY000] [Microsoft][ODBC Driver 17 for SQL Server]SSPI Provider: No Kerberos credentials available (default cache: FILE:/tmp/krb5cc_0) (851968) (SQLDriverConnect)')
(Background on this error at: https://sqlalche.me/e/20/dbapi)
From the research I have done most of what is being suggested to do is to configure Kerberos on the linux machine that is hosting the application. I'm pretty new to Azure, and these serverless functions but my impression is that there isn't like a dedicated machine that is hosting these that I can go and configure as many of the suggestions online I have found are pointing to as a solution.
We have a virtual network set up, and a subnet for the function app. It has been tested by the infrastructure team and has been given the green light that it works and can successfully connect to the on premise infrastructure from Azure Land.
My code:
user = "my_user"
password = "my_pass"
db_name = "my_db"
port = "default_port"
host = "fully_qualified_host"
driver = "ODBC Driver 17 for SQL Server"
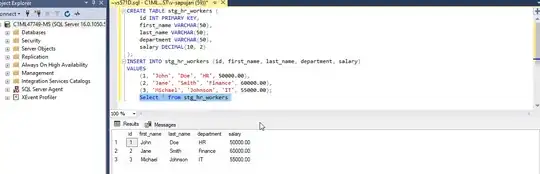
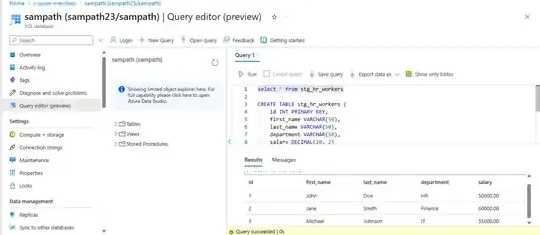
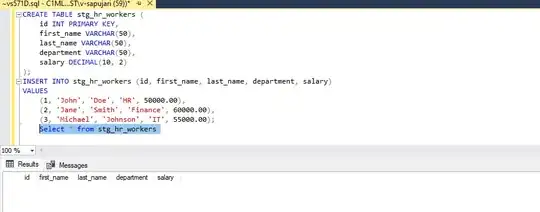
sql_statement = "TRUNCATE TABLE adp.stg_hr_workers"
connection_url = URL.create(
"mssql+pyodbc",
query={
"username": user,
"password": password,
"host": host,
"port": port,
"database": db_name,
"driver": driver
},
)
engine = create_engine(connection_url, echo=False)
Session = sessionmaker(bind=engine)
with Session.begin() as session:
session.execute(text(sql_statement))
When running locally this truncates the table. When hosting in Azure this give the Kerberos credentialing error.