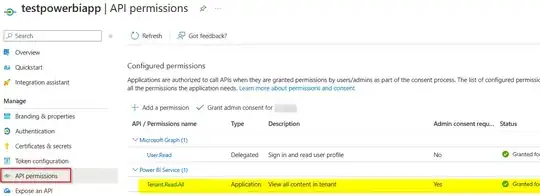
Note that: Client Credential flow works only for Application API permissions.
The "401 unauthorized" error usually occurs if the access token does not contain required roles/scopes to perform the action.
To resolve the error, make sure to grant application type API permission to the Azure AD Application:
I generated the access token using the below code:
var scopesDefault = new string[] { "https://analysis.windows.net/powerbi/api/.default" };
var app = ConfidentialClientApplicationBuilder
.Create("ClientID")
.WithAuthority("https://login.microsoftonline.com/TenantID")
.WithClientSecret("ClientSecret")
.Build();
Microsoft.Identity.Client.AuthenticationResult result = await app
.AcquireTokenForClient(scopesDefault)
.ExecuteAsync();
var text = result.AccessToken;
Console.WriteLine(text);
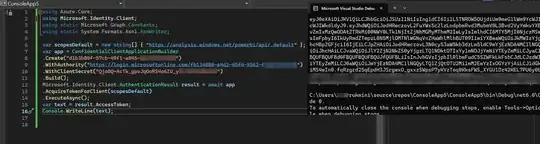
When I decoded access token, roles are displayed:
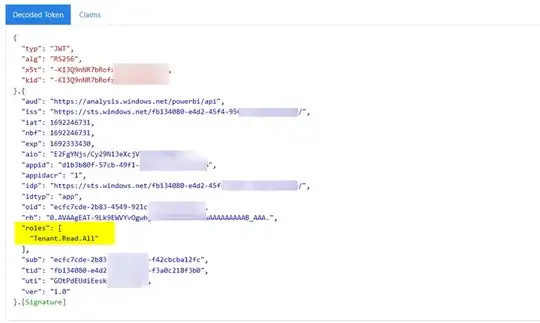
If still the issue persists, check the below:
- Few Power BI operations or accessing Power BI requires only delegated admin access token.
- Based on your requirement you can assign delegated Api permissions and make use of Authorization Code Flow to generate access token.
- Create an Azure Security Group and add the Service Principal as a Member:
Enable Allow service principals to use read-only admin APIs option in Power BI Admin Portal and add Security Group:
References:
Power BI REST APIs for embedded analytics and automation - Power BI REST API
powerbi - Access Token Scope Issue in Azure AD and Power - Stack Overflow by me