How to provide access of ACR to Azure container apps which are not in same network group: -
You can create Private endpoints which allow you to access the container registry directly from your virtual network using a private IP address.
After a workaround on your issue, I found below approach to access ACR from other virtual networks.
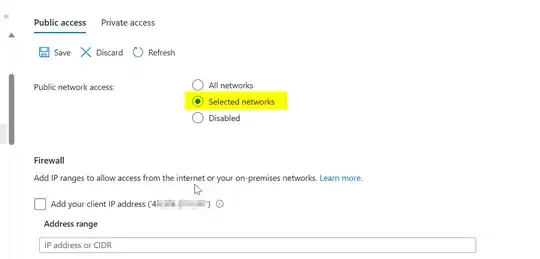
Goto container registry >> Networking >> Choose selected networks and enable firewall by adding which IP addresses to block (if required) >> Enable allow access from trusted >> Click on save.
Alternatively, you can create a identity to the ACR and add the required permissions to the specific managed identity as shown in MSDoc.
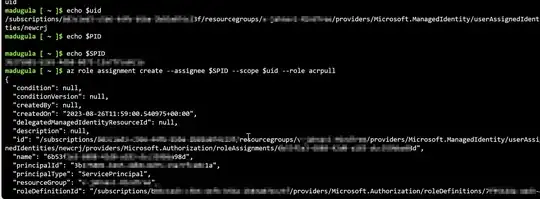
I've created an identity and added permissions using AzCLI:
az identity create --resource-group <resourcegroup> --name newcrj
uid=$(az identity create --resource-group <resourcegroup> --name newcrj --query id --output tsv)
spid=$(az identity show --resource-group <resourcegroup> --name newcrj --query principalId --output tsv)
az role assignment create --assignee $spid --scope $uid --role acrpull
Update:
After a discussion and workaround on your issue, I found that there is no possibility of attaching ACR to the container app without using credentials if it is a private registry.
I tried with all the deployment methods and each deployment is prompting for user credentials for private registries.