I want to disable firebug using on each my webpages. Sometimes , we embedded important keys or id in my ui widgets. Some of our methods from server side will takes these keys for processing. So , someone can edit by firebug. That may cause wrong data updating of our database or wrong data showing in webpages. For security options , I want to disable using firebug or other developer tools of browsers. As GoogleChrome 's home page , when I open firebug in it , I want to show error message as follow..
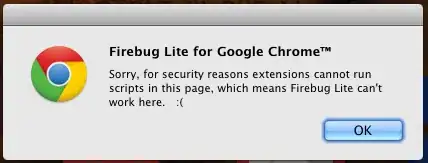
How can I do as like it ? Eg: I want to validate my form datas with JavaScript or such as using with JQuery Form Validation That's fine. But when I use with firebug and delete elements of error messages will become validate this form.How to prevent it !Any suggestions would be appreciated. Really I means not only firebug but also others developer tools, addons , plugins. My question main point is how to disabling them. FireBug in Chrome Browser home page process and validation form instances are examples for I want to do.