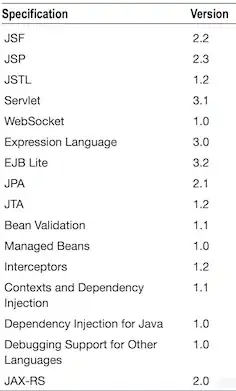
We have a pool of develop machines where developers log in through RDP and usually they doesn't log off but just disconnect. As local administrator I can force the log off but I would like to check when the user disconnected.
From task manager I can see only the user name and its status
Is there a way to discover when the user disconnected using task manager, powershell, cmd or whatever?