How do we enable HTTPS in Amazon EC2? Our site is working on HTTP.
-
3good question, but i set the security group and no charm happens – Shark Deng Jun 01 '20 at 13:05
10 Answers
First, you need to open HTTPS port (443). To do that, you go to https://console.aws.amazon.com/ec2/ and click on the Security Groups link on the left, then create a new security group with also HTTPS available.
Then, just update the security group of a running instance or create a new instance using that group.
After these steps, your EC2 work is finished, and it's all an application problem.
- 10,350
- 3
- 34
- 59
- 1,867
- 1
- 15
- 19
-
15I was able to add a new rule for port 443 to the Security Group used by the instance and it just started working without even rebooting it. – Dmitry Efimenko Sep 08 '13 at 19:29
-
10`you can't change a security group of a running instance, even rebooting` - I think this limitation was removed since this answer was posted. – Yuriy Nakonechnyy Apr 23 '14 at 15:10
-
16You don't need to change the security group, you can `Edit inbound rules` – Khoi Jun 04 '14 at 10:02
-
I'm not sure when it changed, but in 2015 you can have multiple security groups assigned to an EC2 instance, and change these at any time. – chris Dec 20 '15 at 16:55
-
@Yura I have added HTTPS in security group but I am not able to access the site using https://www.test.com where as http://www.test.com is working fine. – nikhil84 Dec 21 '16 at 13:25
-
11@nikhil84 by adding HTTPS in security group you only opened port 443 on the machine which is step 1. Second, you need to setup your server on that machine to listen to 443 port (instead of default HTTP port 80) and accept HTTPS traffic. Which server do you use? – Yuriy Nakonechnyy Dec 22 '16 at 09:49
-
@Yura I'm using aws EC2 instance (Linux OS). Now where do I need make changes for the listener ? I had brought the .com (domain) from another vender and hosting it on aws cloud. In case any more info needed pls let me know – nikhil84 Dec 22 '16 at 09:58
-
@nikhil84 what web server are you using on that machine - Apache HTTPD, Nginx, IIS ? Because you definitely need web server to return you some pages, when you access then via test.com – Yuriy Nakonechnyy Dec 23 '16 at 10:54
-
-
4@nikhil84 please follow guidelines listed here: https://www.digitalocean.com/community/tutorials/how-to-create-a-ssl-certificate-on-apache-for-ubuntu-14-04 to setup https on Apache HTTPD – Yuriy Nakonechnyy Jan 03 '17 at 14:28
This answer is focused to someone that buy a domain in another site (as GoDaddy) and want to use the Amazon free certificate with Certificate Manager
This answer uses Amazon Classic Load Balancer (paid) see the pricing before using it
Step 1 - Request a certificate with Certificate Manager
Go to Certificate Manager > Request Certificate > Request a public certificate
On Domain name you will add myprojectdomainname.com and *.myprojectdomainname.com and go on Next
Chose Email validation and Confirm and Request
Open the email that you have received (on the email account that you have buyed the domain) and aprove the request
After this, check if the validation status of myprojectdomainname.com and *.myprojectdomainname.com is sucess, if is sucess you can continue to Step 2
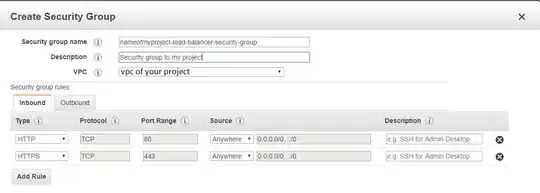
Step 2 - Create a Security Group to a Load Balancer
On EC2 go to Security Groups > and Create a Security Group and add the http and https inbound
Step 3 - Create the Load Balancer
EC2 > Load Balancer > Create Load Balancer > Classic Load Balancer (Third option)
Create LB inside - the vpc of your project
On Load Balancer Protocol add Http and Https
Next > Select exiting security group
Choose the security group that you have create in the previous step
Next > Choose certificate from ACM
Select the certificate of the step 1
Next >
on Health check i've used the ping path / (one slash instead of /index.html)
Step 4 - Associate your instance with the security group of load balancer
EC2 > Instances > click on your project > Actions > Networking > Change Security Groups
Add the Security Group of your Load Balancer
Step 5
EC2 > Load Balancer > Click on the load balancer that you have created > copy the DNS Name (A Record), it will be something like myproject-2021611191.us-east-1.elb.amazonaws.com
Go to Route 53 > Routes Zones > click on the domain name > Go to Records Sets
(If you are don't have your domain here, create a hosted zone with Domain Name: myprojectdomainname.com and Type: Public Hosted Zone)
Check if you have a record type A (probably not), create/edit record set with name empty, type A, alias Yes and Target the dns that you have copied
Create also a new Record Set of type A, name *.myprojectdomainname.com, alias Yes and Target your domain (myprojectdomainname.com). This will make possible access your site with www.myprojectdomainname.com and subsite.myprojectdomainname.com. Note: You will need to configure your reverse proxy (Nginx/Apache) to do so.
On NS copy the 4 Name Servers values to use on the next Step, it will be something like:
ns-362.awsdns-45.com
ns-1558.awsdns-02.co.uk
ns-737.awsdns-28.net
ns-1522.awsdns-62.org
Go to EC2 > Instances > And copy the IPv4 Public IP too
Step 6
On the domain register site that you have buyed the domain (in my case GoDaddy)
Change the routing to http : <Your IPv4 Public IP Number> and select Forward with masking
Change the Name Servers (NS) to the 4 NS that you have copied, this can take 48 hours to make effect
- 5,179
- 2
- 23
- 34
-
4
-
I did all this but I get ERR_CONNECTION_TIMED_OUT when I hit my domain in a browser – Curtis Sep 16 '19 at 08:13
-
1I needed to make a load balancer with a new Target Group on port 80, then edit the listeners to use port 80. Works now. Thanks. – Curtis Sep 18 '19 at 00:54
-
1@Curtis Load balancer is not the only option to use https, you can also configure "lets encrypt" inside your EC2 – Rodrigo João Bertotti Feb 08 '20 at 23:09
-
-
"You will need to configure your reverse proxy (Nginx/Apache) to do so."....so any info on how to do that with this specific example? – Yu Mad Nov 30 '20 at 22:24
-
using a loadbalancer just to serve https is a waste of money and resources. Instead of doing this just set up SSL like you usually would on any server, it will work perfectly fine. – shaki Mar 22 '21 at 08:14
-
-
Amazon EC2 instances are just virtual machines so you would setup SSL the same way you would set it up on any server.
You don't mention what platform you are on, so it difficult to give any more information.
- 18,538
- 4
- 62
- 85
-
1Hello - I'm running a T2.Micro Amazon Linux EC2 instance. I'm using node.js to prop the server up. I am listening to port 443 in my server script and my security group is configured for port 443. What else do I have to do to enable HTTPS? I need a certificate, right? Having trouble finding decent info on doing this that is NOT based on Elastic Beanstalk. – Stephen Tetreault Jan 20 '17 at 21:22
-
2@SMT - take a look at https://letsencrypt.org/ for free and auto-renewing certificates. There is lots of info (via google) on how to set it up using node. There is nothing else AWS/EC2 specific that you need to do. – Geoff Appleford Jan 23 '17 at 08:19
-
2Thanks for the reply! I actually got it working the other day and have streamlined some steps. If anyone is reading this from the future: https://github.com/MSCHF/aws-ec2-node-npm-setup – Stephen Tetreault Jan 24 '17 at 20:14
An old question but worth mentioning another option in the answers. In case the DNS system of your domain has been defined in Amazon Route 53, you can use Amazon CloudFront service in front of your EC2 and attach a free Amazon SSL certificate to it. This way you will benefit from both having a CDN for a faster content delivery and also securing you domain with HTTPS protocol.
- 639
- 8
- 17
-
2Is there any reference or blog where steps are mentioned to achieve this? – Saurabh Yadav Jul 08 '20 at 10:44
-
in this video atiqur rahman get ssl certificate using amazon certificate manager and then he configure cloud front with EC2 instance.After the configuration http/2 is automatically enabled. – Sachithra Dilshan Jul 23 '20 at 09:53
-
You can also use Amazon API Gateway. Put your application behind API Gateway. Please check this FAQ
- 1,489
- 3
- 27
- 45
There must be also an answer for people who want a hassle free https on ec2 for mainly demo and testing purposes, one way they can achieve that very fast is:
With my answer here which describes How you can achieve https for testing purposes in minutes with EC2 without the hassle of creating certificates
- 8,286
- 1
- 43
- 24
One of the best resources I found was using let's encrypt, you do not need ELB nor cloudfront for your EC2 instance to have HTTPS, just follow the following simple instructions: let's encrypt Login to your server and follow the steps in the link.
It is also important as mentioned by others that you have port 443 opened by editing your security groups
You can view your certificate or any other website's by changing the site name in this link
Please do not forget that it is only valid for 90 days
- 63
- 6
You need to register a domain(on GoDaddy for example) and put a load balancer in front of your ec2 instance - as DigaoParceiro said in his answer.
The issue is that domains generated by amazon on your ec2 instances are ephemeral. Today the domain is belonging to you, tomorrow it may not.
For that reason, let's encrypt throws an error when you try to register a certificate on amazon generated domain that states:
The ACME server refuses to issue a certificate for this domain name, because it is forbidden by policy
More details about this here: https://community.letsencrypt.org/t/policy-forbids-issuing-for-name-on-amazon-ec2-domain/12692/4
- 41
- 1
- 6
Use Elastic Load Balacing, it supports SSL termination at the Load Balancer, including offloading SSL decryption from application instances and providing centralized management of SSL certificates.
- 488
- 4
- 7
-
21You don't use ELB simply to provide SSL, that's actually quite a misleading answer. Your server needs to provide SSL regardless, so adding a load balancer is just additional cost if you don't need it. It's also SSL termination in software, so the SSL between the load balancer and server(s) is an additional step, affecting performance. – Frodo Baggins Mar 16 '11 at 09:15
-
1I agree with your comment. It will add additional cost and affect performance. We don't know their exact requirements with respect to load on their servers, so it still might be a way to go. But I do not understand your remark "Your server needs to provide SSL regardless", why is this needed? The load balancer also includes offloading SSL. Thanks. – Peter Hulsen Mar 16 '11 at 10:59
-
2Yes true. You could use that to provide the SSL in a simple fashion. I'm just thinking that the instances still have public DNS values where users could access them directly for whatever reason. If that happened it might well be that you'd want to force that to use SSL too. – Frodo Baggins Mar 16 '11 at 11:03
-
1I know this comment is late, but from my understanding if you want to use a registered domain name, then you have to use ELB, because the EC2 IP is considered 'non-permanent' and therefore cannot use your SSL certificate. On the other hand, if you are just using Amazon's provided DNS, then maybe it doesn't need ELB, I haven't checked. – hexicle Aug 23 '17 at 10:16
-
This answer was valid 11 years ago, and it is still valid. ALB supports installing an SSL certificate in the LB directly, and it will perform SSL termination and send requests to your backend through HTTP. Some comments were and still are VERY wrong and misleading. It's not the best or cheapest way for a single instance, but it will work 100% fine. – Blueriver Feb 16 '22 at 22:45
You need to create a security group for HTTPS and assign it to your webserver:
Open the Amazon EC2 console.
Choose Security Groups in the navigation pane.
Choose Create Security Group.
For Create Security Group, do the following:
For the Security group name, type a name for the security group that you are creating.
(Optional) Type a description of the security group that you are creating.
For VPC, choose the VPC that contains your web server Amazon EC2 instance.
Choose Add Rule. For Type, choose HTTPS.
Choose Create.
In the navigation pane, choose Instances.
Select the check box next to your web server instance. Then choose Actions, Networking, and Change Security Groups.
Select the check box next to the security group that you created for HTTPS. Then choose Assign Security Groups.
To verify SSL/TLS offload with a web browser
- Use a web browser to connect to your web server using the public DNS name or IP address of the server.
- Ensure that the URL in the address bar begins with https://.
- For example, https://ec2-52-14-212-67.us-east-2.compute.amazonaws.com/.
- 2,750
- 1
- 21
- 23
-
3
-
This answer is totally misleading. you either need a load balancer or setup a nginx proxy on your ec2 instance. – EugenSunic Aug 04 '23 at 14:57