Finally .NET 5.0 is released, according to TLS 1.3 support will also be added to .NET beginning with version 5.0 and Microsoft is planning to add TLS 1.3 support to the .NET framework with the arrival of .NET 5.0 tls1.3 works in a .NET 5.0 project.
So i created a test "Console App (.NET Core)" project.
 Then i targeted this project to .net5.0
Then i targeted this project to .net5.0
 Add test code
Add test code
using System;
using System.Net.Security;
using System.Net.Sockets;
using System.Security.Authentication;
using System.Security.Cryptography;
using System.Security.Cryptography.X509Certificates;
using System.Text;
using System.Threading.Tasks;
namespace TestSsl {
class Program {
static void Main(string[] args) {
object locker = new object();
SslProtocols protocol = SslProtocols.Tls13;
Console.WriteLine($"testing SslProtocols.{protocol}");
int port = 1999;
RemoteCertificateValidationCallback certificateValidationCallback = (sender, certificate, chain, sslPolicyErrors) => {
return (true);
};
X509Certificate2 serverCert = new X509Certificate2("server.pfx", "testpass123");
X509Certificate2 clientCert = new X509Certificate2("client.pfx", "testpass123");
TcpListener server = TcpListener.Create(port);
server.Server.SetSocketOption(SocketOptionLevel.Socket, SocketOptionName.KeepAlive, true);
server.Server.NoDelay = true;
server.Server.SetSocketOption(SocketOptionLevel.IPv6, SocketOptionName.IPv6Only, false);
server.Start();
Task taskServer = Task.Run(() => {
TcpClient romoteClient = server.AcceptTcpClient();
Task.Run(() => {
using(romoteClient) {
using(SslStream sslStreamRomoteClient = new SslStream(romoteClient.GetStream(), false, certificateValidationCallback)) {
try {
sslStreamRomoteClient.AuthenticateAsServer(serverCert, true, protocol, true);
byte[] buf = new byte[1000];
int len = sslStreamRomoteClient.Read(buf, 0, buf.Length);
string receive = Encoding.UTF8.GetString(buf, 0, len);
Console.WriteLine($"server receive:{receive}");
sslStreamRomoteClient.Write(Encoding.UTF8.GetBytes("Ok"));
Console.WriteLine($"server send:Ok");
} catch(Exception ex) {
lock(locker) {
Console.WriteLine("======Server Exception==========================");
Console.WriteLine(ex);
}
}
}
}
}).Wait();
});
Task taskClient = Task.Run(() => {
try {
using(TcpClient client = new TcpClient()) {
client.Connect("127.0.0.1", port);
using(SslStream sslStreamClient = new SslStream(client.GetStream(), false, certificateValidationCallback)) {
sslStreamClient.AuthenticateAsClient("127.0.0.1", new X509CertificateCollection() { clientCert }, protocol, true);
string send = "hi, i am testing tls";
sslStreamClient.Write(Encoding.UTF8.GetBytes(send));
Console.WriteLine($"client send:{send}");
byte[] buf = new byte[1000];
int len = sslStreamClient.Read(buf);
string receive = Encoding.UTF8.GetString(buf, 0, len);
Console.WriteLine($"client receive:{receive}");
}
}
} catch(Exception ex) {
lock(locker) {
Console.WriteLine("======Client Exception==========================");
Console.WriteLine(ex);
}
}
});
Task.WaitAll(taskClient, taskServer);
}
}
}
According to how to enable TLS 1.3 in windows 10 i already enabled TLS 1.3 in regedit before
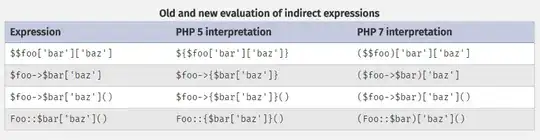
My windows version
How did i create these pfx certificates
CRTPASS="testpass123"
CRTNAME="server"
SUBJECT="/C=DE/ST=test/L=test/O=test GmbH/OU=test/CN=test[${CRTNAME}]/emailAddress=test@test.de"
rm -f ${CRTNAME}.key ${CRTNAME}.csr ${CRTNAME}.crt ${CRTNAME}.pfx
openssl genpkey -algorithm RSA -pkeyopt rsa_keygen_bits:4096 -pkeyopt rsa_keygen_pubexp:65537 -aes-256-cbc -des3 -pass pass:${CRTPASS} -out ${CRTNAME}.key
openssl req -new -sha384 -subj "${SUBJECT}" -key ${CRTNAME}.key -out ${CRTNAME}.csr
openssl x509 -req -days 3650 -signkey ${CRTNAME}.key -in ${CRTNAME}.csr -out ${CRTNAME}.crt
openssl pkcs12 -export -out ${CRTNAME}.pfx -inkey ${CRTNAME}.key -in ${CRTNAME}.crt
openssl x509 -text -in ${CRTNAME}.crt
CRTNAME="client"
SUBJECT="/C=DE/ST=Westerstede/L=Westerstede/O=test GmbH/OU=test/CN=test[${CRTNAME}]/emailAddress=test@test.de"
rm -f ${CRTNAME}.key ${CRTNAME}.csr ${CRTNAME}.crt ${CRTNAME}.pfx
openssl genpkey -algorithm RSA -pkeyopt rsa_keygen_bits:4096 -pkeyopt rsa_keygen_pubexp:65537 -aes-256-cbc -des3 -pass pass:${CRTPASS} -out ${CRTNAME}.key
openssl req -new -sha384 -subj "${SUBJECT}" -key ${CRTNAME}.key -out ${CRTNAME}.csr
openssl x509 -req -days 3650 -signkey ${CRTNAME}.key -in ${CRTNAME}.csr -out ${CRTNAME}.crt
openssl pkcs12 -export -out ${CRTNAME}.pfx -inkey ${CRTNAME}.key -in ${CRTNAME}.crt
openssl x509 -text -in ${CRTNAME}.crt
Before i tested similar codes in a "Console App (.NET Core)" which targeted to ".NET Core 3.1" and it occurred exception "Cannot determine the frame size or a corrupted frame was received"
I would like to know:
1, Does .NET 5.0 already support tls1.3?
2, Is this exception could because my pfx certificates problems?
3, Does windows 10 support tls1.3? if not when will it? i can not find the official plan.
4, How can I use tls1.3 in a UWP project under the current situation?