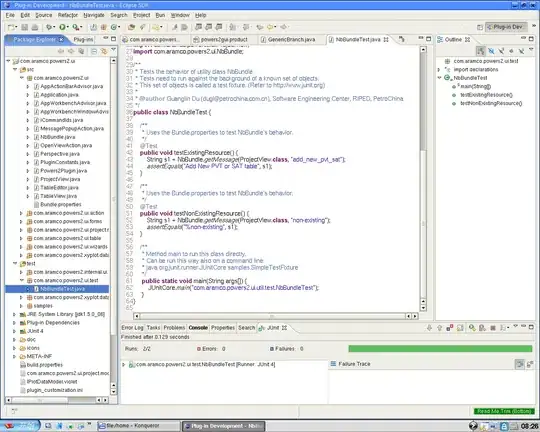
I have x64dbg and ghidra synchronized via ret-sync. I found an interesting point in ghidra:
1800382b1 4d 8b e0 MOV R12,rebitData
1800382b4 48 63 f2 MOVSXD packetSize_,packetSize
in the listing view; the file my.dll starts at 180000000. So, then in x64dbg I add a dll break for my.dll, and when I'm in, I go to the file offset with ctrl+shift+g and enter 328b4, but I end up at (first line):
00007FF8B2FB32B4 | 06 | ???
00007FF8B2FB32B5 | E9 80000000 | jmp my.7FF8B2FB333A
00007FF8B2FB32BA | 45:8BC6 | mov r8d,r14d
00007FF8B2FB32BD | EB 7B | jmp my.7FF8B2FB333A
00007FF8B2FB32BF | 3BFB | cmp edi,ebx
00007FF8B2FB32C1 | 73 22 | jae my.7FF8B2FB32E5
00007FF8B2FB32C3 | 41:3BDB | cmp ebx,r11d
00007FF8B2FB32C6 | 76 18 | jbe my.7FF8B2FB32E0
where in x64dbg, the file starts at: 00007FF8B2F81000 (CPU tab, module my.dll, main thread X, PID Y).
Obviously the instructions are not the same. (I believe I did the rebase correctly)
How can I make the correspondance ghidra -> x64dbg and break in x64dbg at the "same place" ie., same instructions ?